Part 3: CRWD Update - Revisiting The Strategy And Competition With MSFT & S

Summary
- In Part 1 we discussed XDR. In Part 2 we discussed pricing, the channel, and SMB segment. In Part 3 we cover CRWD's competition with MSFT and valuation.
- Specifically, we address the misleading claims that CRWD made against MSFT in its April 2023 investor briefing presentation.
- We speculate on CRWD's future valuation scenarios. In short, there will be range bound opportunities for investors but a multifold upside is unlikely from here.
Taking on MSFT more directly
In the past few years, CRWD CEO has been very vocal about MSFT on the grounds that MSFT is the biggest source of vulnerabilities that trouble the cybersecurity industry today, and MSFT itself is offering a crappy endpoint security product.
Key claims from CRWD slides: (Left CRWD, Right MSFT)
- Advanced AI vs Legacy Signature
- Lower TCO vs High TCO >>> agent bloat and multiple consoles
- 95% of endpoint compromises remediated by CRWD came from MSFT
- 75% of breaches involve a MSFT Defender being bypassed
- MSFT and other legacy vendors still occupy the majority of the market
This is a typical CRWD marketing tactic, whereby some truth is mixed with exaggerated narratives, and on the whole it is quite misleading for investors and customers alike. For example, CRWD historically (and up until very recently) has been 100% focused on only securing the latest Windows OS, and hence, of course, 95% of compromises that CRWD remediates is going to involve a Windows endpoint. Recently, CRWD has reprioritised to give more support to Mac and Linux, however.
Furthermore, as the most popular CRWD deployment is to use CRWD as the EDR while leveraging MSFT's Defender as the EPP on the front-end, it surely makes sense that 75% of breaches that CRWD responds to involves a Defender being bypassed. When the Defender has been bypassed, CRWD detects the attack, but if the Defender detects the attack, it won't show up on CRWD's EDR back-end.
Claims #2 and #3 are cleverly worded for marketing while avoiding any legal battle with MSFT.
On advanced AI, we still struggle to see where CRWD has a true edge over MSFT's incoming OpenAI-powered endpoint security suite. CRWD presumably should have better ML due to its early investments in this vision and the data it has at its disposal. However, if we are to say who wins in AI is the one who owns the best data and algorithm, then most CRWD investors are wrong in pricing-in CRWD's deep moat predicated on its data collection without recognising that MSFT has a 10x+ bigger endpoint security deployment and datasets, and needless to say MSFT has even more diverse sources of data from identity, network, and cloud.
On the TCO claim, this is a weird narrative that is in stark contrast to the prevalent market view that CRWD has a more expensive but highly effective product, while MSFT has a very cheap but moderately effective product. It is to be noted that there is a substantial amount of integration cost associated with deploying the MSFT Defender. However, what CRWD is claiming here is that, because the Defender has a higher risk of breach, even though CRWD is way more expensive on the product level, it is way cheaper if you factor in the probability of asset loss as a consequence of a breach.
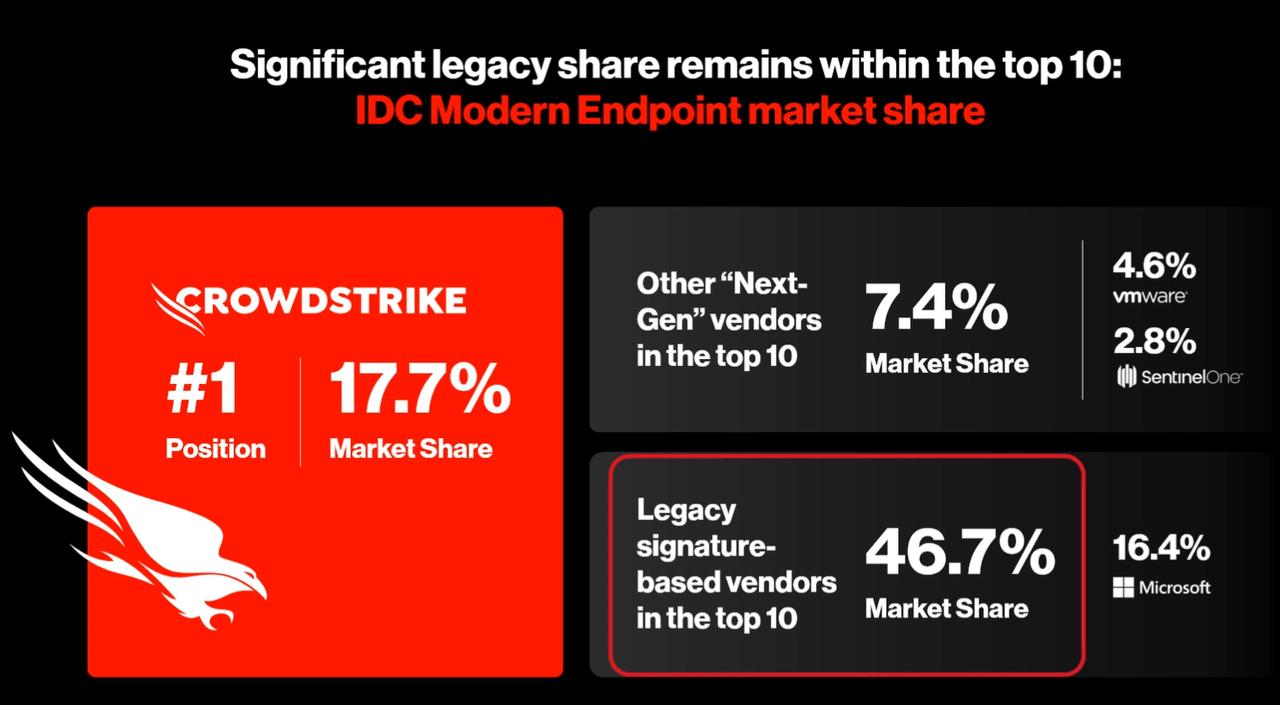
CRWD also listed its market share as 17.7%, which is a very high number for a single vendor in endpoint security industry. Potentially, it could reach the peak penetration of 30%, but we have less confidence it will reach 50% or higher as a big majority of the market still needs signature AV, and a more cost-effective, easier-to-manage XDR without the need to pay hefty fees to human experts.
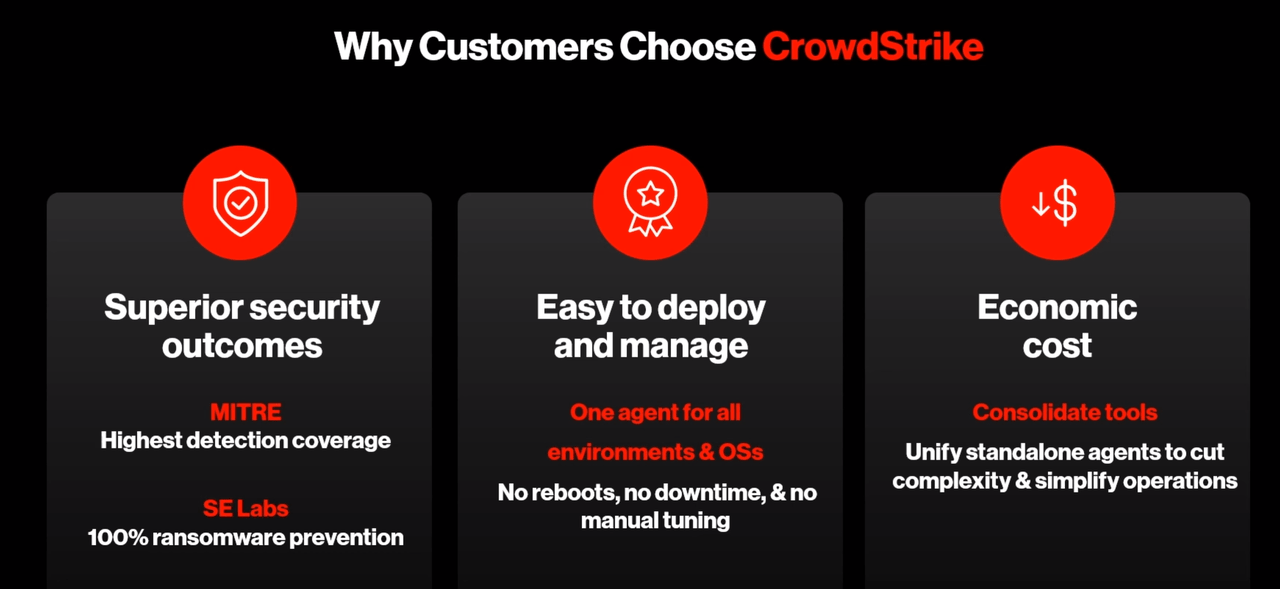
Shown in the slide above, CRWD specifies three reasons why customers choose it. We don't think the superior security outcome makes sense based on our findings and cross-validation with various industry analysts, including Gartner, who pointed out that even though CRWD has touted its security effectiveness, in third-party AV tests, it has very poor results or refuses to release the result to the public. Maybe CRWD is claiming this in relative terms versus legacy AVs instead of the BoB competitors like PANW or S.
In regards to deployment and management, it is also perplexing to see that CRWD say it has the broadest OS support and no downtime or manual tuning. Again, this is a stark contrast to what we have been hearing. CRWD agents performed poorly on Mac and Linux and CRWD was forced to do a revamp ~2 years ago. CRWD requires Kernel-level insertion, which requires a reboot and it is hard to troubleshoot, resulting in longer downtime. It also requires a way bigger team to use the EDR tools that as they are built for human expert operation rather than automated response. It may be the case that it is not easy to manage but certainly easier than legacy AVs that have several disconnected consoles and agents, and many false positives to correlate and reduce.
On the other hand, MSFT doesn't care that much in regards to CRWD's claims as the giant itself is enjoying great GTM into the security business via bundling with its Office 365 E5 bundle. For now, MSFT has more than $20bn ARR from the security business and is growing at c. 20%, and it is planning to invest another $20bn to grow this product line, which is very important to MSFT's future growth. In the recent Ignite 2022 event, the MSFT CEO spent 50% of the time discussing security, and how they have completely streamlined every messy MSFT security product and repositioned them under a unified platform.
MSFT has two primary bundles for its SaaS - Office 365 and Microsoft 365. The former has all productivity suite functions while the latter includes all the enterprise management features such as endpoint security, identity security, data security, IAM, CASB, CSPM, and more. Depending on the breadth, MSFT has F3, E3, and E5 bundles for entry-level, mid-level, and comprehensive inclusion of all MSFT products in one bundle.
The Office 365 E5 is priced at $38 per user per month while the all-inclusive Microsoft 365 E5 is priced at $57 per user per month. So for an additional $228 per year, you get
- a #2 BoB IAM,
- a #2 BoB CASB,
- a first-party BoB CASB for O365 (as MSFT's CASB will be leveraging APIs from MSFT's SaaS applications),
- a good CSPM,
- and a good endpoint security that integrates well with other solutions - Defender for identity, device management, data security, insider risk management, advanced analytics, and more.
And MSFT's claim is true that its E5 license that bundles everything together is 60% cheaper than buying everything individually from BoB point SaaS like G-suite + Slack + Zoom + CRWD + OKTA and more.

More recently, we are hearing from the channel side that MSFT is making great GTM strides in the SMB market. With a weakening economy and the need for cost control, many SMBs pivoted to a consolidated offering from MSFT. This could potentially limit CRWD's market not only on the SMB side but also with enterprise customers who are budget constrained and moving back to MSFT.
There are also several notable developments from MSFT that are worth CRWD investors' attention:
- MSFT licenses are often free but not free for full deployment. Oftentimes there are hefty price hikes as MSFT wants to juice up security ARR as well. Furthermore, it takes a sizeable amount of professional services costs to get MSFT's agent deployed. So, if you factor that in, then the TCO differential between MSFT and CRWD is made smaller by a notable margin.
- Security co-pilot and AI could change the game. MSFT has only introduced GPT4 into the security analytics backend (SOC) of its product line and we believe the real disruption to the industry hasn't come into fruition yet. However, this is a direct attack on CRWD's core niche, which is human expert-centric EDR backend. With security co-pilot, MSFT should have a more level playing field against CRWD, or even better.
- MSFT is not really that legacy. It is constantly evolution and the responsiveness, though slower than CRWD, is still quick and relevant enough to make MSFT's security agile. We are also seeing great interest to adopt MSFT's newly launched Sentinel EDR product. If Sentinel EDR is able to compliment the Defender on lateral movement security in a similar vein to what CRWD does, then CRWD could lose more revenue. This is also probably the reason why CRWD is putting MSFT at the top of the attack list, because CRWD is hearing a lot about MSFT as a huge threat from both investors and customers.
Conclusion
To conclude, here are our takeaways:
- CRWD's pivot to a 100% XDR vision is very important and accretive for shareholder value. Investors should expect a slower decay in CRWD growth as the CEO is still up to the game and dealing with the competition actively. As an EDR turned XDR vendor, CRWD still has closer ties to EDR rather than XDR-native, which could potentially limit its ability to be a winner in the future of XDR.
- CRWD's refocus on SMB and channel partners should help it generate incremental growth without higher S&M spending. Historically, CRWD has chosen to forfeit these two important growth vectors due to conflicts with its strategy. CRWD is having a more balanced emphasis on first-party and third-party services, and coming from 0% channel friendliness to 20% would be welcomed by partners in the beginning and boost its growth. However, over the longer term, we don't see CRWD's channel strategy attractive compared to what its competitors are doing.
- CRWD's new pricing strategy is a 1:1 copy of S'. This should help it compete more directly with S. However, the downside is that the days of easy DBNR via selling premium modules is gone. CRWD will have to rely more on increasing the volume (endpoints deployed) rather than ASP (price per endpoint) as the way to grow.
- CRWD's dominance over MSFT is overblown. MSFT remains a huge threat to CRWD especially in the whitespace that it is targeting for future growth. Investors should note that any positive development from MSFT could pose serious competitive threat to CRWD, especially from SMB and cash-strapped enterprises.
To gauge CRWD's investment potential, let's have some quick calculations: