Investor Guide To SASE (Pt. 1)

Summary
- In Part 1 of Convequity's Investor Guide to SASE, we discuss the things for private and public investors to consider as the SASE market evolves.
- We also share the new Convequity Impulse for SASO (that's not a typo), where we have adapted the Gartner's MQ to better serve investors' interests.
- And we also discuss the consolidation that has been happening in the SASE market and how it will affect the market leadership.
- Finally, in Part 1, we dive into the technical aspects of the SASE components and discuss in which areas certain vendors have an advantage.
- In Part 2 (published later this week), we'll provide a detailed overview of each SASE competitor, discussing strengths, shortcomings, and valuation considerations.
SASE Investor Considerations
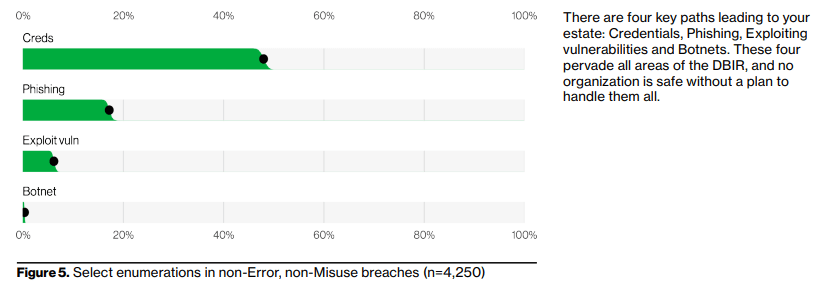
Gartner forecasts the SASE market will reach c. $15bn by 2025 at an annual CAGR of 36%. SASE is a very intriguing market because it is highly disruptive yet the underlying components of SASE are maturing which is leading to quickly increasing adoption rates.
The market is also consolidating. Therefore, investors from the public and private realms, alike, will benefit by understanding the consolidation trends and which vendors will most likely prevail as long-term SASE winners.
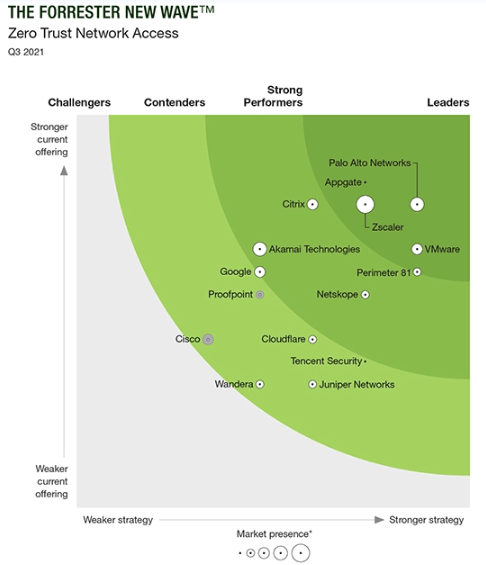
In 2020, we were short-term bullish but long-term avoid/bearish thesis on Zscaler (ZS). We were short-term bullish because ZIA and ZPA - respectively, ZS' cloud-based Secure Web Gateway (SWG) and its Zero Trust Network Access (ZTNA) solutions - were perfectly suited to the changes brought by COVID-19. We also fully appreciated the incredible GTM presence that Jay CHaudhry had cultivated at ZS. As a result of having the ideal solutions and highly effective GTM, ZS became one of the hottest stocks during the pandemic. However, we have been long-term avoid/bearish because we view ZS as having weaker leadership, talent, innovation, and technology than next-gen competitors.
As ZS' bull run lasted longer than we expected, there were moments when we questioned our long-term thesis. We thought that perhaps the GTM can indeed compensate for the weaker technology for many more years to come and discredit the avoid/bearish thesis. However, there are now signs emerging that are validating our long-held views.
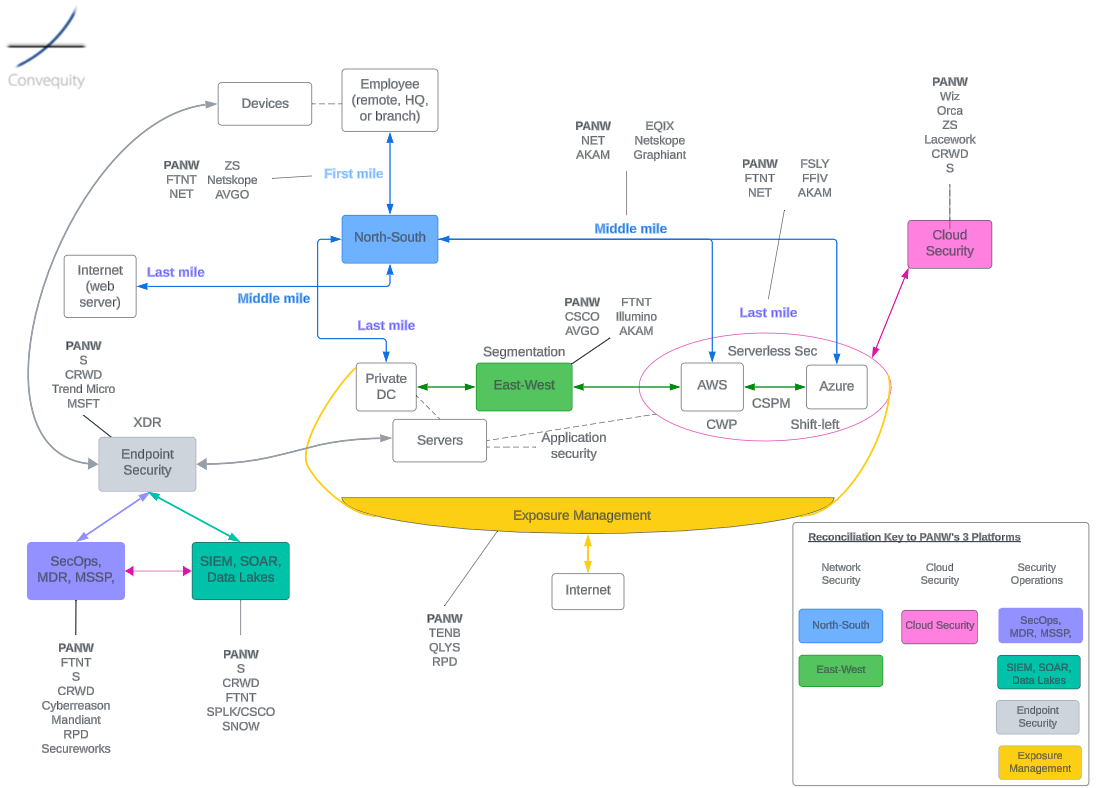
Figure 1 – February 2021 Convequity’s SASE Competitor Analysis
For those interested, here are our past reports on ZS in chronological order.
Zscaler Equity Research Report (Oct 2020)
Founders Comparison: CHKP's Shwed Vs PANW's Zuk. What It Means For Zscaler (Apr 2021)
Pre-IPO: Netskope - Better Quality Than ZS (Dec 2021)
Though, ZS’ 2020/21 SASE success was also largely a case of being ‘in the right place at the right time’. When the lockdowns occurred, out of the entire SASE suite (defined by Gartner in 2019), the cloud-based Secure Web Gateway (SWG) became the most important. This was simply because knowledge workers spend most of their time on the Internet (more so than SaaS or internal applications), and hence when they shifted to working remotely, it made sense from many angles to give them direct secure access to the Internet. ZS had the most mature, tested, and well-known cloud-based SWG available, and therefore, en masse, enterprises made a beeline for ZS.
Being the market leader in cloud-based SWG gave ZS a solid footing to sell enterprises other SASE solutions. Jay Chaudhry’s masterful salesmanship was also key. He has been incredibly successful at building relationships with C-level executives and with channel partners, enabling a slick top-down GTM strategy. His influence to closely align ZS to Gartner’s SASE definitions was also hugely important for ZS’ success. However, now the tide is slowly turning. SWG is evolving to a next-gen era involving SaaS, more granular controls, and Remote Browser Isolation (RBI), but ZS is not innovating fast enough. Furthermore, while SWG and ZTNA are still hugely important, the future of SASE success appears to be more tied to CASB, an area of SASE in which ZS is very poor.
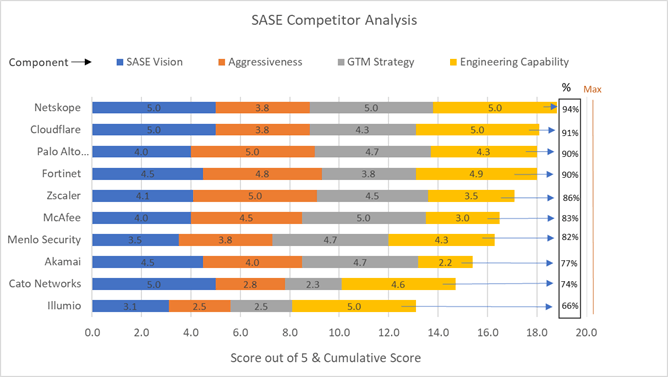
With this in mind, ZS looks destined to have its SASE leadership slip away in the future. For over two years we’ve been critical of ZS and very impressed with Netskope, and finally we feel somewhat validated by Gartner’s latest SSE Magic Quadrant (MQ). Data-centric cybersecurity appears to be the future, and Netskope is without doubt the pioneer in applying this philosophy. ZS, on the other hand, is not. To us, it’s clear that ZS has been so focused on adhering to Gartner’s SASE ideology that, in some ways, they’ve forgot to think for themselves. Blindly following Gartner is not recommended because it will lead to a lack differentiation.
Those that have stubbornly refused to perfectly align with Gartner often end up becoming a standard setter. FTNT and PANW serve as a few of examples here. In the mid-to-late 2000s, FTNT diverged from the typical network firewalls Gartner covered in its MQs, and created a differentiated approach called UTM, or Unified Threat Management, which integrated a broader set of features and targeted the more cost-conscious SMB segment (and FTNT has carried on with this highly integrated approach to security ever since, developing its Fabric platform to be arguably the most interoperable cybersecurity platform around). Following FTNT’s success with its UTM, in 2009 Gartner decided to begin a UTM MQ series.
In a similar vein, PANW created the NGFW market to better target the needs of enterprises with the ability of handling larger amounts of traffic. They also incorporated granular user and application controls which, at the time, was very far removed from typical firewalls that could only exert control over ports and protocols (and ever since PANW has continued to pioneer in application-level control, something that has enabled the company to remain highly relevant as a firewall vendor over the years and enabled it to succeed in adjacent emerging submarkets such as ZTNA and CASB). Subsequently to PANW’s launch of its NGFW, lo and behold Gartner created a new MQ named the Enterprise Network Firewall.
It could also be put forth that FTNT was the first to usher in the concept of converged networking and security, many years before Gartner introduced SASE in 2019. There are probably good examples in APM (e.g., DDOG), SIEM, endpoint security (e.g., S), and others, whereby those opinionated vendors with different or opposing visions to Gartner end up being finally validated in a big way.
The point we’re trying to make here is that it could be Netskope’s turn to be the standard setter for SSE and SASE more broadly, by leading the way with its data-centric approach. And this could be happening at the most opportune time because SASE has transitioned from the infancy to early-mature stage, which means the customers that were previously hesitant toward SASE (and there are still lots of those) are now willing to make the transition.
No doubt Netskope will be a high-profile IPO – whenever that may be – but for those investors that understand we’re witnessing the emergence of a new and special network security leader, will be better equipped than others to assess the company’s value. In a previous post we suggested that, if Netskope and ZS were similarly priced, and as an investor you can access Netskope's secondaries, then a long/short would be a very favourable trade. This would have been a good trade back in February, as the EV/S of the two companies were around 11x. However, at the time of writing ZS' has since declined to ~8x, erasing the alpha of this pair trade. For those qualified investors eligible to trade secondaries, if ZS recovers sufficiently from its recent fall, then this pair trade might present another opportunity.
Aside from the ZS and Netskope investor implications, investors should note PANW, NET, and Broadcom (AVGO) from the SSE MQ. PANW has made it into the Leaders quadrant for the first time, validating their incredible transition from being primarily an on-prem network vendor only a few years ago. Gartner’s recognition for PANW is huge because there are still large portions of network security buyers who wrongly assume they are just an appliance vendor. This could be the catalyst to push PANW ahead of ZS in annual revenue for SASE.
NET’s first-time recognition in the SSE MQ is a key milestone. They needed to acquire Vectrix, an out-of-band CASB startup, in order to gain the CASB capabilities, as the company’s home-grown CASB didn’t progress as initially planned. This is common to see when network guys with expertise in inspecting data in transit are then trying their hand at inspecting data at rest via APIs – simply because it requires a whole different skillset and approach to security. Nevertheless, NET now has the full set of SSE and SASE capabilities, and importantly they have recently revamped the leadership of their sales organisation to execute a top-down GTM strategy. The initial execution of NET's revamped GTM has been far below expectations, but presuming it will eventually at least be moderately successful, then NET has a decent runway into the enterprise market to extend its period of high growth and help maximise margins.
AVGO might be the vendor that surprises the market the most, however, especially if the $61bn VMW deal goes through. AVGO is vertically and horizontally integrated, having Broadcom’s ASIC networking chip, Symantec’s SSE, and, if Broadcom can satisfy regulators’ demands, VMware’s SD-WAN (acquisition of VeloCloud) and endpoint security (acquisition of Carbon Black). We would go as far as saying that AVGO has the best SDN (Software-Defined Networking) chip and VMW has the best SDN software - which provides substantial amounts of future innovation thanks to SDN being the foundation for other technologies such as SD-WAN and greatly improves the efficiency of other tech such as NFV (Networking Function Virtualisation). VMW also has the second biggest SD-WAN market share.
This stack could really accelerate the speed of SASE while providing a mature security platform from Symantec that has great data security built in with a very good data classifier. An added bonus is the value coming from Carbon Black’s endpoint security repertoire that can help improve the efficacy of any SASE implementation. And from a GTM perspective, AVGO already has everything in place to execute a successful top-down and channel driven strategy, as it has a great presence among large enterprises.
For PEs and VCs, Skyhigh Security, Forcepoint, and Lookout are also interesting to monitor. Gartner has positioned these in the Visionaries section because they each have a differentiated approach to SSE which may prove to be highly successful. Iboss is another name for PEs/VCs to watch as they execute their long overdue enterprise GTM strategy. In our opinion, CSCO is the only uninteresting name that has few opportunities for SASE-interested investors. CSCO has a history of acquiring BoB startups and then stifling the innovation and there is way too much technical debt to overcome to be a leading SASE vendor. Having said that, CSCO will remain a presence purely by virtue of its colossal customer base that it can sell SASE into. Even if they did emerge as a leader, given the size of CSCO’s revenue base it is not going to be a significant catalyst for the stock price.
In the later sections of the report, we shall diver a little deeper into each SSE and SASE vendor, discussing strengths and weaknesses.
Convequity Impulse for SASO
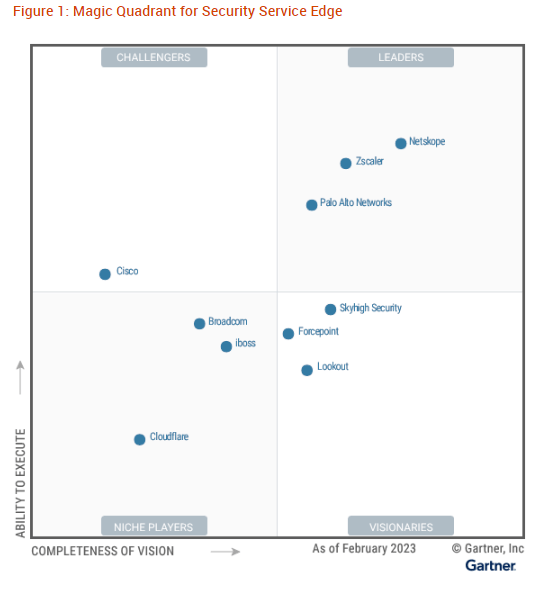
Before we dive into the key SASE components and share our opinion on each SASE vendor's competitive strengths, shortcomings, and valuation considerations, here is the Convequity Impulse for SASO, or Secure Access Service Omni. This is an adaptation of Gartner's SASE definition and Gartner's Magic Quadrant. The dictionary definition of 'omni' is 'all or everything or everywhere'. So, in this context, omni means delivering converged security and networking in all form factors, not just in the cloud PoP, as is the case for Gartner's SASE. Hence, SASO includes converged security and networking conducted off-prem in the cloud, on-prem in appliance or VM form, and remotely for home office use cases.
Cloud-delivered isn't always 100% the best option for enterprises with complex hybrid environments. Furthermore, tech innovation will continue to sway from decentralisation to centralisation, and vice versa, and as some aspects of cloud are maturing at the same time that vendors and customers are looking for ways to increase performance, in the future it's likely the edge will attract more attention. This more expansive definition for converged security and networking is useful for investors because it shines the light on other promising vendors that are either discarded or not fully appreciated by Gartner and its SSE and SASE framework. The more expansive definition of SASO will include and/or place more recognition on names like Cato Networks and FTNT, for example, that are not present in Gartner's SSE MQ.
The two dimensions are Market Adoption (x-axis) and Product Strength (y-axis). Scoring each vendor against these dimensions is based on the present. The horizontal arrow indicates Convequity's assessment for the vendor's future market adoption over the next two years. An arrow pointing to the right indicates an increase in market share over the two-year horizon, and an arrow pointing to the left indicates a decrease in market share over the two-year horizon. The level of current Product Strength has been the main factor in assessing the future market adoption. The other important factor for forecasting future market adoption is the vendor's product roadmap. As highlighted, a green circle signals the vendor has a strong roadmap, and a red circle signals the vendor has a weak roadmap. This is an important factor because there are many vendors in which we've scored lower on current Product Strength, but it's not the case that they will experience poor market adoption if they have a strong product roadmap.
As we will lay out in this report in the following sections, we anticipate that CASBs, DLPs, RBI, SD-WAN, converged security-driven networking, global network performance, and endpoint SASE-related compute, are the most innovative areas. Therefore, vendors with portfolios well suited to these SASE trends will score relatively higher on the Product Strength dimension. Additionally, those vendors with strong roadmaps related to these SASE trends have received a green circle. In turn, current product strength and product roadmap have an impact on the direction and the length of the arrow along the Market Adoption dimension.
Intro to SASE
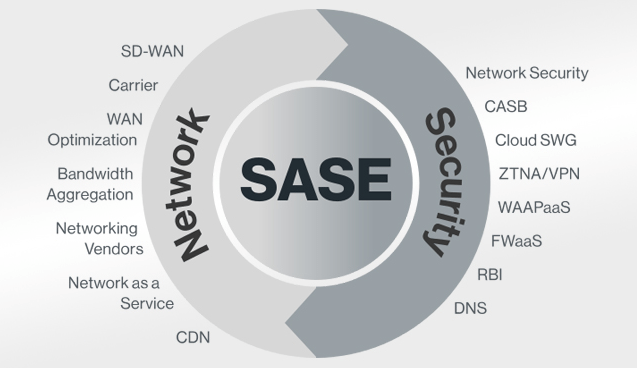
What is SASE?
SASE, or Secure Access Service Edge, continues to grow its presence across network security. For hybrid and distributed enterprises, it delivers a variety of benefits as they consume networking and security as a service, in replace of managing an array of different on-prem appliances themselves. Benefits include:
- Scalability: the SASE networking/security stack can easily scale to handle an increased load, accommodating the growing needs of a business without requiring significant infrastructure upgrades or investments.
- Cost savings: organizations can reduce capital expenditure on hardware and infrastructure, as well as operational costs related to maintenance and upgrades. Subscription-based pricing models can offer more predictable costs and better financial flexibility.
- Automatic updates: SASE is continuously updated with the latest software and threat intelligence, ensuring up-to-date protection against evolving security threats. This eliminates the need for manual updates and reduces the risk of human error.
- Remote access: SASE enables secure access to company resources from any location, making it easier to support remote workforces and branch offices.
- Reduced complexity: Deploying and managing a cloud-based platform is often simpler than the equivalent on-prem solution, as it doesn't require dedicated hardware installation and complex network configurations.
- High availability: SASE, as with most SaaS solutions, is typically designed to offer high availability and redundancy, minimising the risk of downtime due to hardware failure, power outages, or other issues that may affect on-prem solutions.
- Faster deployment: Implementing SASE is usually faster than deploying an on-prem networking and security stack, as it doesn't require physical installation or configuration of hardware.
- Flexible: thanks to SASE being delivered as a service, adding and removing solutions within the SASE stack is relatively frictionless, enabling enterprises to be flexible to changing requirements.
- Integrated services: While SASE includes a wide range of services, it is also able to easily integrate with third-party solutions outside the scope of SASE.
- Global threat intelligence: SASE leverages the collective intelligence of multiple organisations and data sources, providing more accurate and up-to-date threat detection and protection.
- Easier compliance: SASE can help organizations achieve compliance with various data protection and privacy regulations, as the service providers often have built-in security measures and certifications that meet regulatory requirements.
Essentially, SASE is a converged networking and security platform that replaces complex on-prem deployments. Typically, an on-prem-centric enterprise will have numerous different appliances for networking and security, such as the router, firewall, load balancer, WAN optimizer, Secure Web Gateway (SWG), SD-WAN, VPN connector, and Data Loss Prevention (DLP). Traffic passes through each of these, adding latency to the end user. Additionally, each of these need to be periodically updated, upgraded, and reconfigured, adding operational burden to IT administrators. The idea underpinning SASE is to converge all these functions into one networking/security stack to reduce the associated latency and increase performance. Furthermore, the SASE stack resides in the cloud or edge PoP to provide multitenancy benefits such as availability and scalability, and also means that maintenance and upgrades are all handled by the SASE vendor.
On the security side, SASE should include solutions like SWG, RBI, ZTNA, CASB, and FWaaS. On the networking side there are also several solutions but the most important solution is SD-WAN. This is because to use SASE, enterprises can no longer just rely on their MPLS network, they must transmit traffic securely over the Internet. SD-WAN is a software-defined approach to managing a network whereby a centralized control plane remotely programs routers to securely forward traffic along the most optimal paths toward its destination. Those optimal paths may take a more cost-effective Internet route or a faster MPLS route, subject to application requirements. So, SD-WAN greatly enhances overall network performance - better managing costs while also ensuring applications get the optimal paths and bandwidths so that users receive a great experience and can be maximally productive.
Market Confusion
Shortly after Gartner introduced SASE in 2019, vendors, from networking and cybersecurity alike, made a beeline for the nascent but promising market. In desperation not to miss out on the opportunity, many vendors quickly promoted themselves as SASE without having the adequate technology and architecture.
This resulted in mass confusion across the market because many security vendors claimed they had the full SASE stack, but during the subsequent implementation the customer would discover that they require integrations with third-party vendors. For example, a security vendor marketing SASE may still require on-prem firewall integration because they did not have FWaaS in their SASE stack. Probably the most common deception was claiming a full SASE capability but then subsequently explaining to the customer that SD-WAN needs a third-party vendor integration. The lack of upfront clarity inevitably led to higher costs than what were initially estimated, which no doubt has had a suppressing effect on the market’s growth to date.
From SASE to SSE
In early 2022, in what looks to be an attempt to address the confusion, Gartner decided to separate out the security components of SASE and publish a Magic Quadrant (MQ) report named Secure Service Edge, or SSE. In some ways the move makes sense because SD-WAN is already covered in Gartner’s WAN Edge Infrastructure MQ, hence doing a SASE MQ (including security & SD-WAN) would have generated more confusion. The other option would have been for Gartner to discontinue its WAN Edge MQ and publish a SASE MQ that includes security and SD-WAN. However, the resulting breadth would not have translated into very digestible content for Gartner customers.
Not only did Gartner remove the networking components, they also greatly narrowed down the scope of the security side. SSE includes just SWG, ZTNA, and CASB, which respectively, includes:
- users on the corporate network connecting to the Internet via forward proxy
- remote users connecting to internal applications hosted at the corporate data centre
- on-prem and remote users connecting to SaaS applications in the cloud
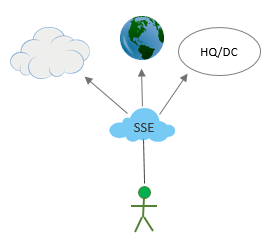
The move appears to have further elevated the market thanks to it now being clearer for customers. Converged off-prem network security is SSE which includes SWG, ZTNA and CASB, and converged security and networking is SASE which includes SSE plus SD-WAN predominantly.
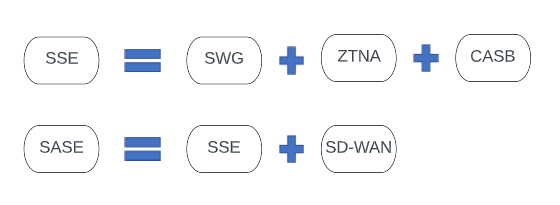
This is good for market adoption, but as we point out in this report, the vendors who blindly follow Gartner’s guide are unlikely to prosper as long-term winners. Therefore, vendors that differentiate with their own vision and a roadmap to develop the deepest stack and broadest set of capabilities across both security and networking will likely be the long-term winners as the market evolves.
Consolidation (and impact on ZS’ Leadership)
During the first few years, SASE customer deployments entailed multiple vendors. This was attributed to the market confusion and to the fact that vendors entered SASE coming from various backgrounds, which resulted in customers selecting BoB vendors for the different aspects of SASE.
ZS was one of the earliest SASE promoters but only had SWG and ZTNA and needed to develop CASB and integrate with third-party SD-WAN vendors to deliver the networking side. PANW claimed SASE but lacked the cloud-based security stack and didn’t have SD-WAN. Albeit less aggressively, FTNT also claimed SASE, being the only security vendor to have in-house SD-WAN, but lacked the cloud-based security stack. Consequently, in the earlier days, customers aiming to deploy SASE ended up having multiple vendor solutions stitched together.
In an odd way, having Gartner hone in on just SSE has galvanised the broader SASE market. Last year, Broadcom set the wheels in motion to acquire VMware which will combine Symantec’s SSE and VeloCloud’s (VMware’s earlier acquisition) SD-WAN into a full SASE stack. Last year, Netskope acquired SD-WAN vendor Infiot to offer a full in-house SASE platform. In March 2023, HPE acquired Axis Security which will most likely be combined with Silver Peak’s (HPE’s earlier acquisition) SD-WAN to form a full SASE. Then, there is standalone SD-WAN Versa that is developing its own SSE suite to offer full SASE too. The market is consolidating both ways: SSE to SD-WAN and SD-WAN to SSE. If you take a look at the following SD-WAN MQ (formerly named WAN Edge Infra MQ), you’ll notice every leader now has its own SSE solution.
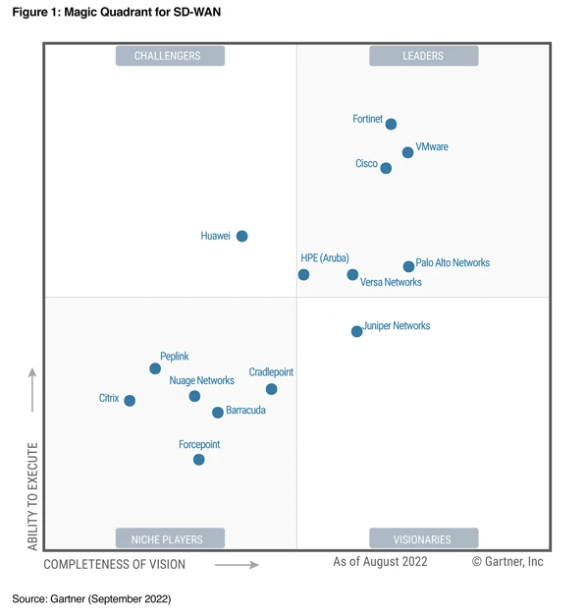
These vendors now join the few other vendors, such as FTNT, PANW, and CSCO, that offer a full in-house SASE platform. Now customers have ample choice for choosing a single vendor for their SASE deployment, which will bring a variety of benefits including greater performance and easier administration.
The one leading vendor missing out on the consolidation trend is ZS. Without obtaining an in-house SD-WAN capability (either via M&A or home-grown), it is difficult to envisage ZS gaining a stronger foothold in the SASE market. Influenced by the SASE consolidation, in September 2022 Gartner published its ‘Market Guide for Single-Vendor SASE’, and predicted that by 2025, 50% of SD-WAN purchases will be part of a single SASE vendor solution, up from 10% in 2022. They also forecast that one-third of new SASE deployments will be based on a single vendor, again up from 10% in 2022. This really does marginalise ZS’ leadership in SASE and greatly curtails its SAM (Serviceable Addressable Market).
SWG
SWG can be a legacy hardware appliance that sits on the edge of the corporate network or be a cloud-based SaaS solution. It protects enterprises from online threats, reduces unproductivity, and prevents data loss, as employees use the Internet. To protect against online threats, SWG vendors update a list of malicious and suspicious sites and block access to them. To limit unproductive usage of the Internet, the SWG can block or allow access to certain sites, such as social media, subject to employees’ roles at the company (which was probably the biggest value proposition because buyers could see an instant ROI from a productivity standpoint). And to prevent sensitive data from leaving the enterprise, DLP (Data Loss Prevention) technology is applied to identify and block certain file types from being uploaded or transmitted to the Internet.
SWGs are an imperative component in the security stack to protect against phishing attacks, which represent roughly one-fifth of all cyber attack vectors. In essence, phishing is an attempt by the attacker to have you click on a malicious link. Those links may be waiting on websites for users to click or most commonly are delivered via email. When the link is clicked which generates a connection request to the web server in question, the SWG will (hopefully) detect that it is either a known bad URL or a suspicious URL, and prevent the connection.
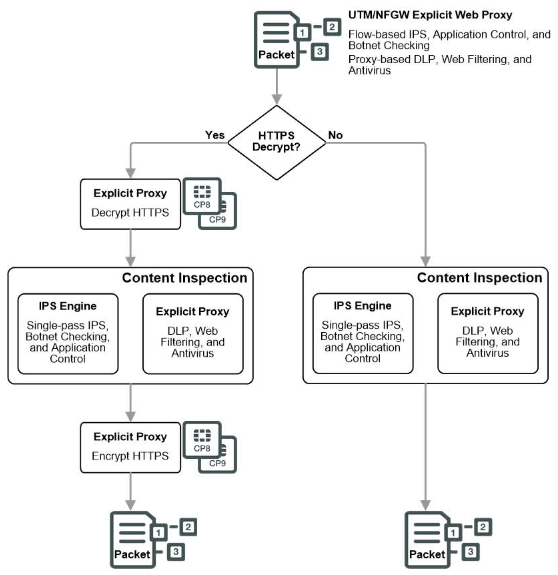
SWGs operate as forward SSL (the encryption standard for HTTPS) proxies, meaning they protect clients (users) as they connect to the Internet by being an intermediary between the client and server. In other words, they pose as the server to the client and the client to the server, so there is no direct connection to potentially malicious URLs. Subsequent to establishing one connection with the client and one connection with the server, the forward proxy generates a new SSL certificate for the requested domain, signed by the proxy's own Certificate Authority. This new certificate is presented to the client as if it were the server's original certificate. The forward SSL proxy is then established as the intermediary and will decrypt and re-encrypt all packets flowing between the client and server to check for sensitive data transmission and malicious code/URLs.
There has long been a debate on whether firewalls or forward proxies are more important for protecting a corporate network. This debate has particularly intensified between PANW and ZS over the years. In practice, however, both technologies compliment one another.
Firewalls operate at Layer 3 and 4 of the OSI Reference Model. They control access to ports (e.g., port 25 for email, port 80 for HTTP, port 443 for HTTPS, and port 3389 for RDP) to provide the security basics and make sure attackers can’t enter the network via exploiting one of the 65k ports on a server or computer. SWGs operate at Layer 7, but as they are web gateways by nature, they only handle HTTP, HTTPS, FTP, and XMPP.
Before the encryption era, firewalls were the better option. This was because they could perform deep packet inspection (DPI) on data flows without breaking the client-server connection. This provided a much better end user experience compared to the proxy-based SWGs that need to break the client-server connection and then establish two connections simultaneously. Firewalls have greater flexibility as they can allow traffic for specific ports to pass through without a heavy duty and high latency proxy. Furthermore, with the advent of next-generation firewalls (NGFWs) and Unified Threat Management (UTM) devices, DPI also inspected Layer 7 to better understand the content and context of network packets and gain more insight at the application level.
However, during the mid-2010s, mass encryption and the shift from HTTP to HTTPS increased the importance of proxy-based SWGs. NGFWs couldn't perform DPI without decryption first, so in effect they began to operate similar to proxies for encrypted traffic.
In the early 2010s, most NGFWs vendors (e.g., PANW, FTNT) subsumed the functionality of SWGs, which really marginalised on-prem SWG vendors such as then-SWG market leader, Blue Coat. Blue Coat got further marginalised when ZS emerged with a disruptive cloud-based SWG that delivered all the SASE benefits outlined earlier – from cost savings, to scalability, to easier deployments, updates, management, and ultimately overall better security efficacy. So Blue Coat essentially lost a lot of business to both PANW and ZS - losing out to PANW for on-prem SWG business and losing out to ZS for those orgs wanting to transition to a cloud-delivered SWG.
ZS’ advantages became even clearer when enterprises became increasingly distributed, having more employees in remote locations and more applications hosted in the cloud. It no longer made sense to backhaul remote users’ Internet-bound traffic to an on-prem SWG, when they could simply use Zscaler to reach the Internet directly.
In 2016, Blue Coat was acquired by Symantec to broaden Symantec’s enterprise security offering. Then, in 2019, chipmaker Broadcom acquired Symantec to extend its own enterprise-focused networking and security platform. Symantec and Broadcom have done an adequate job at adapting Blue Coats technology into a cloud-based SWG. They have also succeeded in adding ZTNA and CASB to complete an SSE offering, gaining recognition in Gartner’s SSE MQ. However, Blue Coats adaptation to the changing landscape has been far too slow, allowing ZS to generate great momentum to become the undisputed SWG market leader.
Influenced by Gartner’s unveiling of SASE in 2019, ZS began expanding into ZTNA, CASB, and FWaaS to market themselves as a SASE vendor. The ramifications of the COVID pandemic helped ZS gain even greater momentum as entire workforces were ordered to work from home. With a mature cloud-based SWG at the core of its SASE offering, ZS was well-positioned to cross-sell the other SASE components and quickly emerge as the number one leader.
The general trend for modern cloud-based SWGs has been for more granular control over what users can do as they interact with websites (i.e., download, upload, post). They have also evolved to expand the same controls to SaaS applications. Though, the biggest step-change in SWG innovation has been the Remote Browser Isolation, or RBI, technology.
A cloud-based SWG with RBI will render the packets received from the web server and then stream the pixels through to the client. In other words, instead of the client’s browser rendering the web page, the cloud-based RBI will render the web page and then stream the pixels. This creates an air gap between the corporate network, and its endpoints, and the Internet, making it impossible for attackers to execute their malicious code in the users’ browser. RBI has been around for many years but adoption has been slow due to the intensive compute and high bandwidth required to stream the pixels. Early RBI solutions generated unacceptable latency and very poor user experience (e.g., lots of jitter, clicking a button doesn’t work, etc.).
RBI solutions have improved over time thanks to the general improvements in compute and networking. However, a major advancement in RBI has been that of local rendering. In essence, this next-gen approach to RBI separates the execution from the rendering, thereby executing the web page on the cloud-based server to search for malicious code, but sending unrendered packets to the client’s browser to be rendered. Doing RBI this way requires less bandwidth and availability.
Here is an example comparing pixel streaming to local rendering:
Pixel streaming >>> send the entire screen, fully rendered, consisting of 10 words of content in 1080p to the client browser. This equates to transmitting 2 million pixels which is almost equivalent to a 4MB image.
Local rendering >>> send the 10 words unrendered in 1080p to the client browser. This is equivalent to transmitting only 10KB of data.
A simple analogy might be to consider the manufacture and shipping of a large machinery item. Option A (e.g., for server-side rendering plus pixel streaming) is the company could manufacture the machinery in their home country and then ship the finished product to the customer located in another country. Option B (e.g., for local rendering) is to ship the machinery flat-pack to reduce space (equivalent to reducing the required bandwidth) along with the blueprint, and assemble the machinery in the customer’s country. Option B requires less bandwidth which translates to lower costs and lower latency.
The most innovative players in the RBI space are Menlo Security and NET. In 2020, NET acquired a local rendering RBI startup named S2 Systems which applies a novel approach to local rendering with a patented solution named Network Vector Rasterization, or NVR. It involves utilizing the Skia library, which is an open-source graphics engine incorporated into the Chromium engine (the engine NET also uses for its Workers edge compute platform). Basically, S2 intercepts the Skia-based draw commands, compresses and encrypts them, and then transmits them to the client browser for local rendering. NET’s RBI is also clientless, meaning no agent is required on the endpoint.
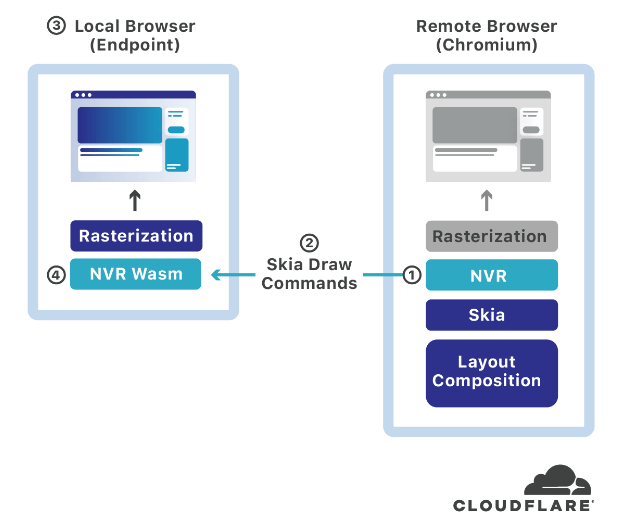
Only Menlo Security is in the same league as NET with respect to RBI. They also leverage local rendering, using something called DOM Mirroring, but have a more mature RBI with a wider array of adjacent features. In 2019, ZS acquired Appsulate, an RBI startup that is less cutting-edge as they have taken the pixel streaming approach – i.e., executing and rendering in the server-side remote browser. Unlike NET and Menlo Security, ZS has no information on their blog for technical readers to learn the specifics about their RBI. In our opinion, this is a telltale sign that the company is aware they do not have the BoB approach to RBI.
PANW has partnered with an RBI specialist named Ericom to incorporate RBI into its Prisma SASE platform. Netskope acquired a startup named Randed, which laid the technological foundation for its RBI solution. However, these are server-side rendered plus pixel streamed RBI solutions, thereby by design they suffer from high costs and subpar user experience. Forcepoint, McAfee (now Skyhigh Security in SSE MQ), and Symantec (now Broadcom in SSE MQ), were each too early in acquiring RBI startups (c. 2017-19). As a result, they now have the pixel streaming RBI tech that is clearly inferior to those solutions that incorporate local rendering.
If local rendering is the key for accelerating RBI adoption, then NET and Menlo Security have great advantages in becoming the NG-SWG leaders. It is unlikely that other SWG vendors opting to go the server rendered route will be able to rearchitect their product and catch-up NET in a timely manner.
The web browser is one of the most complex systems to secure. Its original purpose at the dawn of the Internet was to simply display text documents. Since then, it has evolved to handle multimedia, various third-party plugins, and a variety of functions which provide great user experience but creates many weak spots for attackers to exploit. Hence, it requires a huge amount of time and resources for a vendor to integrate effective security that doesn’t impact user experience. Furthermore, a vendor contemplating local rendering RBI will need to consider the multiple different browsers, each with many different operating systems and different versions in production.
Taking into account the RBI-related M&A since c. 2017, it’s clear the required expertise is at such a high level that it is more cost effective to acquire than build in-house. So, unless ZS acquires another RBI startup it is difficult to envisage them matching NET and Menlo Security on the technological front, and therefore, they will likely lose their leadership in the SWG market.
ZTNA
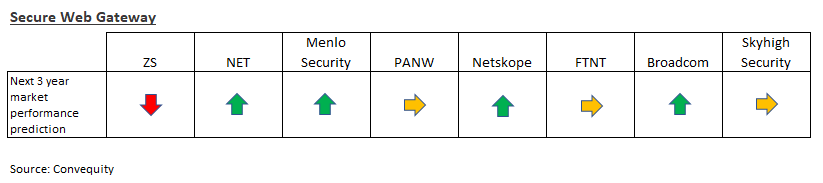
Zero Trust Network Access, or ZTNA, provides an encrypted connection between a user and the internal application they are accessing. The concept of Zero Trust was created in 2010 by John Kindervag during his tenure at Forrester Research. It is a security framework that adopts the principle of "never trust, always verify". This means that no user or device, whether outside or inside the network, is inherently trusted, and access is granted based on strict identity verification and context-aware policies.
Prior to the Zero Trust model, and ZTNA more specifically, any person already connected to the network – whether someone physically on-prem or someone remotely connected via VPN – could access IT resources without authentication. In other words, in this framework it is assumed that if the IP of the device indicates the user is on the network, then there is an implicit trust present and the user can access the whole network. Not only does this make an organization vulnerable to malicious and negligent insider behaviour, any attacker able to enter the network has unrestricted access to roam around in search of valuable data and systems.
ZTNA was designed to establish a secure connection between a user and the application only, thereby removing access to the wider network. This greatly limits the ability for attackers to infiltrate and then move laterally across the network. The other major security design of ZTNA is that applications configured to the ZTNA are completely invisible to unauthenticated users. This means traditional network scanning conducted by bad actors is futile because the IP address is hidden.
Despite the concept being around since 2010, it wasn’t until the latter parts of the 2010s when Zero Trust gained wide interest, attributed to workforces becoming increasingly mobile and remote. The repercussions of the pandemic generated a new surge of interest as all workforces became remote. As a consequence, during COVID, ZTNA quickly emerged as the VPN replacement for accessing internal resources. Not only do VPNs grant network-wide access, they also suffer from limited bandwidth, processing power, and scalability given that they are on-prem appliances. Thus, user experience can drastically decline during traffic spikes. ZTNA offerings, being delivered as gateways in the cloud, proved to be not only more secure but way more scalable too, thereby unaffecting user experience.
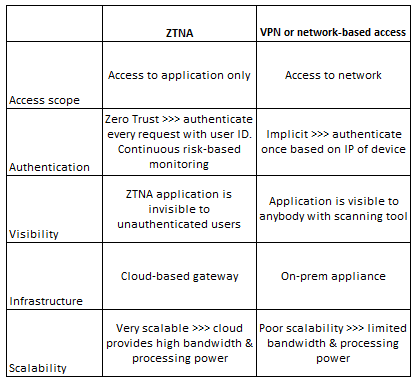
It is worth noting that while ZTNA has helped enterprises become more secure, architecturally, ZTNA is actually similar to VPN but just on a per-app basis. So, while ZTNA was needed, there was a degree of hype built in.
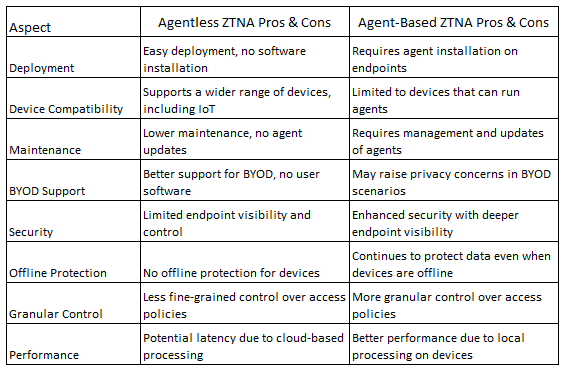
That hype has calmed down somewhat over the past few quarters, however, as ZTNA reaches the early stages of maturation. But there are still ways for vendors to differentiate and there are still architectural choices for customers to make. Providers have varying capabilities across device posture, mobile experience, visibility, user experience, contextual data, identity provider integrations, access control granularity, continuous verification, ease of deployment, and others. Some providers of ZTNA deliver it with an agent installed on the endpoint, others deliver it as an agentless service by putting more of the brains in the cloud – and some vendors offer both agentless and agent-based ZTNA. Also, some providers combine ZTNA into the same agent as other apps (which saves disk space), whereas others can only deliver ZTNA in an agent on its own. Some integrate ZTNA into the SD-WAN router and/or SD-WAN agent. The point here is that there are plenty of opportunities for leading ZTNA players to still innovate, differentiate their offerings, add greater value, and generate incremental growth.
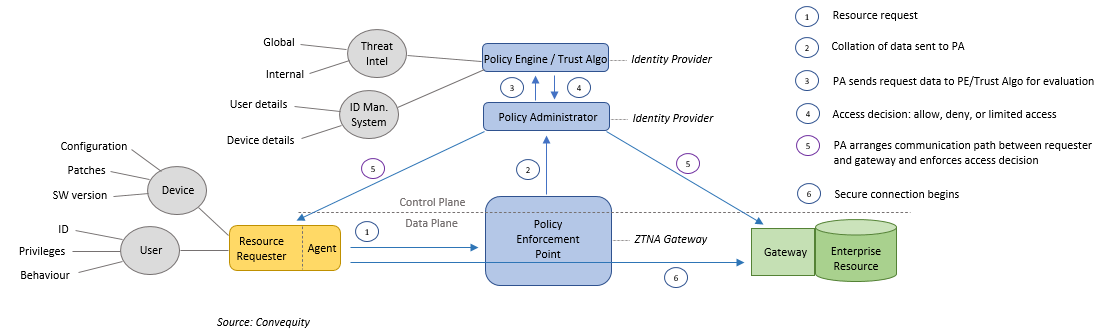
Below is a diagram showing the steps following a user (or machine) making a request to access an enterprise resource (app, system, etc.). The diagram is based on an agent + gateway ZTNA model as we think it’s likely that this version will prevail as the most popular due to the amount of contextual data (time, location, user behaviour patterns, device’s configurations, etc.) that can be delivered by having an agent on the endpoint. As can be seen, a ZTNA is software-defined, as on the network device (labelled as the Policy Enforcement Point, aka the ZTNA Gateway) the control plane is separated from the data plane, thus meaning the policy for all network devices can be centrally controlled.
This software abstraction also provides an additional layer of security because the control functionality is no longer located on the network device. When a resource request has been made, the data pertaining to the user and device is sent from the PEP (i.e., the ZTNA Gateway in the cloud) to the PA (Policy Administrator) and then to the PE (Policy Engine) - in fact, most of the time the PA and PE are combined together as one as they will be managed by the identity provider.
The PE will analyze the user and device data in conjunction with global and internal threat intelligence, throw all the data into the Trust Algorithm, and then make an access decision accordingly (full or limited access, or reject). Once access has been granted by the PE, the PA will construct the pathway between requester and the gateway of the resource (which will likely be a specialized VM-based firewall) that goes through the ZTNA gateway.
The quality of the security and user experience is highly dependent on the quality of the ZTNA vendor’s integrations with the IdP (Identity Provider). The ZTNA vendor needs to interoperate with open-source protocols such as SAML and OAuth and various APIs used by the IdP in order to support MFA and SSO technologies, which are important for facilitating secure and seamless access to applications. Many legacy vendors, with technical debt entangled in fully closed-source monolithic architectures, have struggled to deliver superior ZTNA because of their historical lack of openness. This is why cleaner slate names, such as Perimeter 81, that leverage open-source protocols and rich API connectivity have achieved success in ZTNA against the larger legacy network security vendors.
Cleaner slates do offer an advantage in Zero Trust; however, firewall vendors have also had an advantage. Despite being an innovation, as previously mentioned ZTNA's architecture is some ways is similar to VPN. It is also based on old protocols, and those protocols have long been heavily used by firewall vendors. As previously mentioned, ZTNA makes applications invisible to unauthenticated users, even if they are facing the Internet. This is achieved by incorporating SPA (Single Packet Authentication) into the ZTNA. SPA is a passive authentication process that requires just a single encrypted packet to be sent to the firewall positioned in front of the application. The packet is decrypted with a public-private key pair and contains information about the user, device, and resource requested. If the authentication is successful, then the firewall temporarily opens the appropriate port to establish the user to application connection.
The simplistic ingenuity of this is that by default all the ports controlled by the firewall are closed, and hence the application is invisible. It only becomes visible once the authentication with SPA is complete and the relevant port opens up. This is kind of a reversal of the standard TCP/IP process which involves a connection being established with a series of SYN & ACK messages before authentication begins.
SPA is an evolution of the earlier port-knocking authentication process that entailed a sequence of packets being sent to a number of different ports. For example, the firewall may have required single packets being sent to following ports in order, 21400 1051 2603 62201, before opening the relevant port and establishing a connection between user and application. Port knocking has served a purpose but is vulnerable to DoS attacks, which is why SPA has emerged to replace it and become integral to ZTNA.
To summarise, the link between ZTNA and firewalls is very clear because ZTNA incorporates SPA which is an evolution of port knocking and its efficacy is completely reliant on the ability of a firewall. This is why leading firewall vendors, such as PANW and FTNT, were so quick to deliver a leading ZTNA solution. These vendors also have way more experience in controlling all ports and protocols, unlike SWG vendors that moved into ZTNA having experience in only ports 80 and 443 for HTTP and HTTPS beforehand.
Despite, ZS not having the firewall heritage, they too were able to quickly develop a market leading ZTNA solution, named ZPA. In hindsight ZS success in ZTNA is a surprise because the company’s origins are in SWG technologies (and SWG is a forward proxy), which in some ways is the polar opposite to ZTNA (which can be regarded as a reverse proxy because it protects applications from incoming connections outside of the network). SWGs use the standard SSL/TLS encryption and certificate process which verifies that the server is a trusted entity. Though, this standard configuration of SSL/TLS is not enough for ZTNA because it doesn’t verify that the client is a trusted client. Therefore, something called mutual TLS is required for ZTNA to verify the client is trusted on behalf of the server, as well as verifying the server is trusted on behalf of the client. So, for ZS, ZTNA was initially security that was quite far removed to the company’s core competence.
Nonetheless, ZS has delivered a market leading ZTNA product. And one reason for this is that fwknop, which is a system for implementing SPA, has strong support on FreeBSD, which is the operating system ZS uses for its products. This might be a tedious link; however, it is possible that this is what gave them an advantage when they decided to develop a ZTNA solution.
PANW’s very quick success in ZTNA was also a result of its GlobalProtect solution. GlobalProtect was a VPN architecture designed to extend the capabilities of PANW’s next-generation firewalls to remote users and devices. GlobalProtect already incorporated user and device authentication, as well as context-aware access controls, and was designed with a large amount of scalability. So, PANW leveraged these capabilities to implement a ZTNA model and incorporate continuous evaluation of user identity, device context, and other factors to make fine-grained access decisions.
PANW’s successful expansion into Zero Trust was also assisted by the appointment of John Kindervag. The creator of the Zero Trust concept worked at PANW as Field CTO from 2017 through 2021. It’s probable that the Forrester connection also helped PANW become a leader in Forrester’s Wave for ZTNA in 2020.
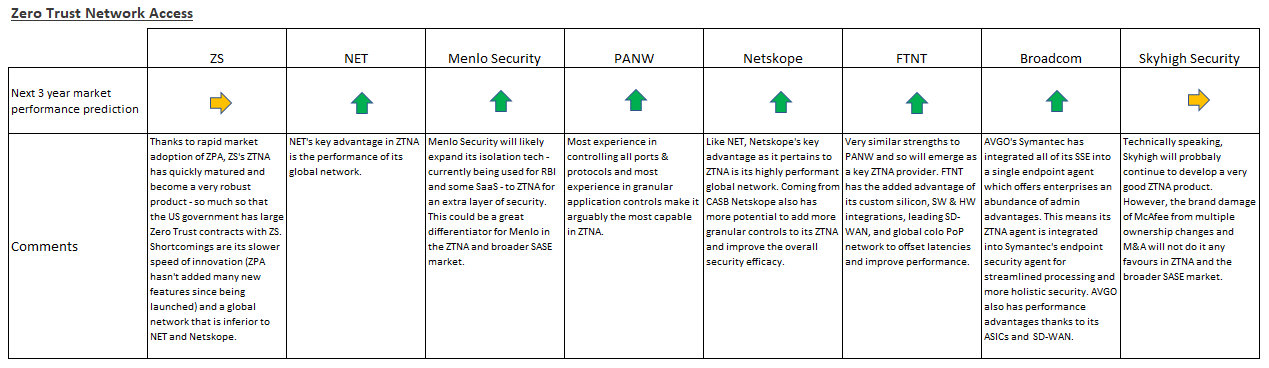
Judging ZTNA as a standalone market, we would say PANW has the best tech and market opportunities. Agentless ZTNA has its advantages but agent-based ZTNA will likely prevail as the standard implementation because the treacherous cybersecurity landscape is forcing enterprises to prioritise endpoint visibility, security efficacy, and granular access controls over other aspects. Due to PANW’s investment in endpoint security, it has clear advantages in developing a lightweight and highly capable agent. PANW’s ZTNA agent is incorporated into its Cortex XDR agent for endpoint security. Then, there is the ZTNA integration with their market-leading NGFWs and GlobalProtect. All of this indicates that PANW will be a net winner in ZTNA going forward.
However, ZTNA requires continuous identity verification which adds substantial latency to user experience. Therefore, investors interested in picking the future ZTNA winners should consider the performance and availability of vendors’ global networks. NET and Netskope, with their highly performant global networks, are clear considerations here. FTNT is another consideration thanks to its custom silicon ASICs and SD-WAN that can both offset significant amounts of latency introduced via ZTNA.
CASB
A Cloud Access Security Broker is a software solution that governs what SaaS applications employees can use. Shadow IT is a big problem that raises many security vulnerabilities whereby users begin using and sharing confidential data with SaaS applications that have not been IT approved. CASBs prevent users from using such unsanctioned SaaS applications in order to gain more control over the usage of an enterprise’s data. CASBs also granularly govern what users can see and do when using sanctioned SaaS applications subject to their roles and responsibilities. Hence CASBs are very important for reducing the attack surface (via blocking unsanctioned applications) and enforcing a least-privileged access model (via granular access control within sanctioned applications).
CASBs first came to market around 2011/12 in out-of-band form, meaning the CASBs leveraged the APIs of the CSPs and the SaaS providers in order to monitor user activity and detect policy violations. By using APIs, they can also monitor data at rest and block the transfer of any sensitive data. However, these out-of-band solutions were limited in their ability to prevent or mitigate threats in real-time, as they relied on periodic API calls and could only analyze data after it had been processed by the cloud service. These limitations became more pronounced in tandem with the growing usage of cloud and SaaS services.
As organisations started to store more sensitive data in the cloud and faced a growing number of security threats, the need for real-time protection became critical. In the late 2010s, inline CASBs (that operate as proxies) emerged to address this need by intercepting and inspecting network traffic between users and cloud services in real-time. These inline CASBs can enforce access control, data loss prevention, encryption, and other security policies before the data reaches the cloud service. This allows organizations to better protect sensitive data, prevent unauthorized access, and mitigate threats as they occur.
From a technical perspective, it is the inline form of CASB which is part of the SSE stack. However, the out-of-band CASB competencies are also assessed by SSE customers and Gartner alike, as the technology is essential in securing enterprises in the new era of distributed IT. As the CASB market has evolved, hybrid CASBs have emerged to incorporate the best of both out-of-band and inline CASB functionality. Hybrids combine real-time protection with continuous monitoring and policy enforcement, to enable organizations to better manage and secure their cloud services.
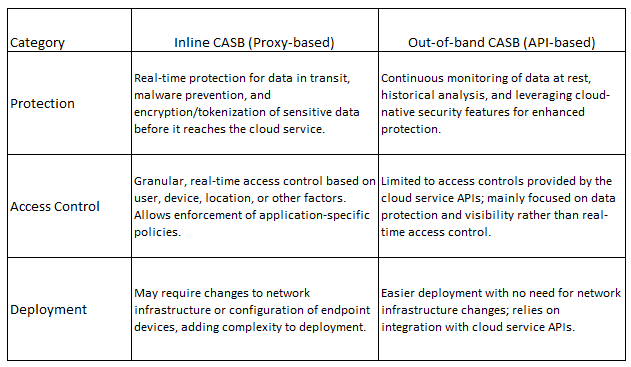
It is interesting to ponder which background is better suited for inline CASB. Are the advantages with the network security vendors that have the inline inspection experience? Or are the advantages with out-of-band CASB vendors that have the SaaS monitoring experience?
In our opinion, we would say the advantages are with the latter, as understanding SaaS applications and the data associated with these applications is where most value is added. This explains why Netskope has been so successful at expanding from out-of-band to inline, and ultimately providing a hybrid CASB, whereas NET, which comes from an inline security (and networking) background, has really struggled to build an in-house out-of-band CASB. NET’s home-grown out-of-band CASB was in beta for approximately two years, didn’t make sufficient progress, and hence they were compelled into acquiring Vectrix in early 2022.
By connecting the dots, it seems as though having out-of-band capability is a prerequisite for developing an inline. Not only did NET need to acquire Vectrix to then integrate and help develop its inline CASB (ultimately leading to being included in Gartner’s SSE MQ), back in 2019 ZS acquired Cloudneeti, which was a CSPM startup by definition but had expertise in data protection which was quickly integrated into ZS’ out-of-band and then inline CASB.
With these thoughts in mind, it seems as though out-of-band CASB players may have the upper hand in SSE. Arguably the array of knowledge required for CASB is greater than SWG and ZTNA, because they need to interoperate with thousands of SaaS applications. Presumably this is why the CASB market quickly consolidated in the late 2010s, as larger security names didn’t have the time to develop the extensive knowledge to build a home-grown CASB.
Players originating from CASB are also likely to benefit from the growing usage of ChatGPT in the workplace. ChatGPT poses huge data security risks and standard inline DLPs incorporated into SWGs and inline CASBs are currently incapable of detecting and stopping the copying and pasting of sensitive data into the chatbot. Netskope’s DLP, however, is able to prevent the pasting of confidential data into ChatGPT and other chatbots.
“In essence, the widespread usage of ChatGPT increases the odds of data leakages by orders of magnitude. Most DLP solutions (either those incorporated into CASBs or those that are legacy on-prem) are designed to identify and block the transfer of certain files and certain recognizable PII (e.g., SSN, credit card numbers, passports, etc.). They would not be able to detect the innumerable nuances, ambiguities, and interpretations of confidential data fed into ChatGPT. Therefore, at present the high majority of orgs are at an elevated risk and urgently need to consider the roadmap of their incumbent DLP vendor, or consider going with a BoB DLP vendor. This is why we believe Netskope has a huge opportunity as they have the best DLP solution in the market. As CASB is a major component of the SASE market (actually 1 of the 3 components of Secure Service Edge, or SSE), Netskope’s prowess in advanced data security could be a game changer in the wake of ChatGPT.” ChatGPT SASE Catalyst for Netskope, Convequity’s Substack.
Netskope is the standard setter in the CASB space, so as the importance of CASB grows within SSE and SASE, Netskope’s new found leadership will only extend (subject to effective GTM execution). The other key differentiator for Netskope is that apart from Skyhigh Security, all the other SSE MQ vendors are from either network or endpoint security area. If a data-centric security approach is the future then Netskope is ideally positioned. And it appears that this is the way the cybersecurity market will evolve because ultimately data is the currency that bad actors are trying to steal. It is inevitable that cybercriminals will get to sensitive data, but if you can ensure the data cannot be moved, corrupted, encrypted or destroyed without proper authentication and authorization, then this could be the most important layer of the security stack.
Furthermore, there are no shortcuts in becoming an expert in handling data. There are countless types of data, countless ways data can be accessed maliciously, and countless ways to protect and govern data. The knowledge scope is incomparable to that of standalone SWG vendors that primarily handle HTTPS and approved and blocked URL lists - which can actually be bought from merchant filtering list providers, enabling most network administrators to create a barebone SWG (it's just that it won't scale well). Netskope has over 3000 data identifiers for over 1500 file types to manage this diversity, which is not something other SASE vendors will be able to easily replicate.
Netskope actually leverages its pioneering DLP technology across ZTNA and SWG too, thereby providing enterprise customers with a converged and highly optimised SSE platform. It is expected that over time this synergy can improve security efficacy, increase network performance, and lower down costs more than competitors.
Other SASE Components
FWaaS
FWaaS is a highly scalable cloud-based firewall with NGFW features, such as Intrusion Detection & Prevention and application control. The limelight has been on other security solutions within the SASE and SSE stack, though firewall services are still very much needed because they provide a security baseline. Without control of which ports are open and which ones are closed, an org would be extremely vulnerable to attacks.
Additionally, like on-prem NGFWs, FWaaS can handle the full range of ports and protocols. They can also add notable efficiencies to network operations by allowing certain types of unencrypted and encrypted types of traffic to pass through uninspected. For example, certain applications might be sensitive to proxies that break the connection to decrypt/reencrypt network packets, or certain confidential data pertaining to health, finance, or government, may need to remain encrypted from source to destination.
In these cases, a firewall, or FWaaS, can step in to allow the confidential data or application traffic to pass through without DPI, but can still make use of the unencrypted parts of a packet such as the user's IP address, the user's location, the size of the data packets, and any state related to the frequency of connection with the application, in order to make some security checks and make a threat assessment.
A SWG needs to decrypt and reencrypt each and every packet, so it is far less flexible. This is why ZS and other vendors with the SWG background decided to develop FWaaS capabilities. So, NGFW vendors have come into SASE with certain advantages related to being able to provide baseline security, a very broad range of protocol and port control, advanced intrusion detection/prevention, while at the same time provide NetOps efficiencies.