Convequity Cybersecurity Taxonomy (Pt 2.1)
Summary
- Since our initial release of Part 1 of the Cybersecurity Taxonomy, we have made some minor updates which we will explain in the opening paragraph.
- We are mindful we have published a lot of content related to network security recently. Therefore, please come forth with content suggestions.
- FYI, we do have a deep dive on CFLT on its way and other non-cybersecurity content in the next few weeks.
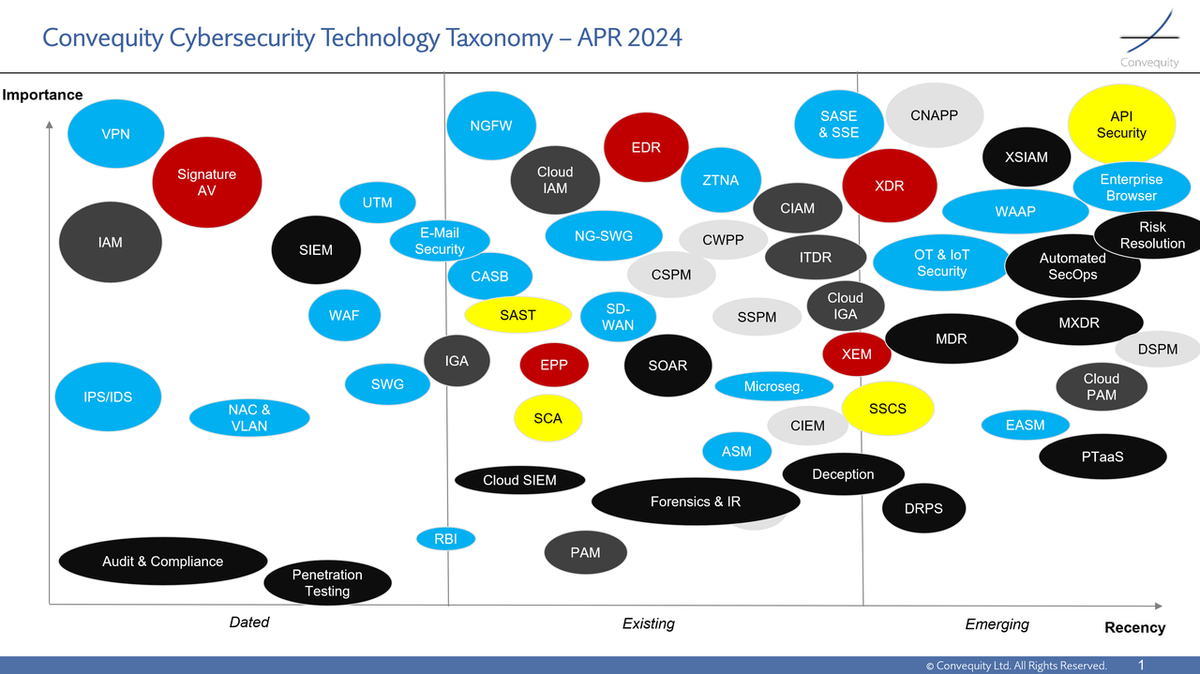
Convequity Cybersecurity Taxonomy
Since our initial release of Part 1 of the Cybersecurity Taxonomy, we have made some minor updates. Originally, when we released Part 1 in the summer of 2023, the series was going to be a five-part series, the first part being an overview/introduction, and each subsequent part covering the four main categories of cybersecurity: network security, cloud security, SecOps, and identity. However, we have so much to share on network security alone, that Part 2 is going to have a number of sub-parts. Hence, this is why this report is Part 2.1, the remaining network security reports being Part 2.2 and Part 2.3.
In Cybersecurity Taxonomy Part 2.X, we're diving into network security history, current industry trends, and key technologies. In Part 2.1 we are going to provide a brief history of network security and touch on how the current key players have evolved.
As a quick reminder, in Part 1 we distilled the industry into four primary categories:
- Network Security (blue)
- Cloud Security: Real-time protection & Shift-Right (dark yellow); Shift-Left (light yellow)
- Security Operations: SecOps (dark red); Endpoint Security (light red)
- Identity (green)
In Part 2.X we'll be diving into Network Security and its own sub-taxonomy. For those new to the topic, we recommend listening to our podcast with Stock Universe on Network Security to gain a general understanding of the landscape.




