Recap: Palo Alto Networks - SASE, SASO, & Beyond
Summary
- We did say we would pause from publishing more network security content for a while, and we do have alternative content on the way. Though, this is a free article we have published elsewhere. It serves as a recap to our previous Palo Alto Networks content and we think it's worth a read, even for those who are now more familiar with the company.
- In this free article, we review Palo Alto Network's prospects in networking and network security via the same framework we applied to Fortinet in our last free article.
- SASE is all about the first mile of transit for a data packet. However, there are the middle and last miles for investors to consider, as the focus of the industry will likely evolve and expand from SASE.
- Compared to FTNT, PANW is in a weaker position amid this broader view of networking and network security. However, we are still bullish long-term thanks to PANW's other areas of cybersecurity.
- Hence, in this article we will recap on PANW's prospects in SASE, SASO, and beyond, that is, the broader networking/network security landscape, and save discussion on cloud security and SecOps for another time. Though, if you have questions that need immediate answers, send us a comment at the bottom of the report or email us at service@convequity.com
Leveraging Breadth for the New Plaftormization Strategy
Since 2022, Palo Alto Networks (NASDAQ:PANW) has presented its business as three divisions, that are now referred to as platforms – Network Security, Cloud Security, and SecOps. Each division has acquired a significant number of leadership accolades from market analysts, such as Gartner and Forrester.
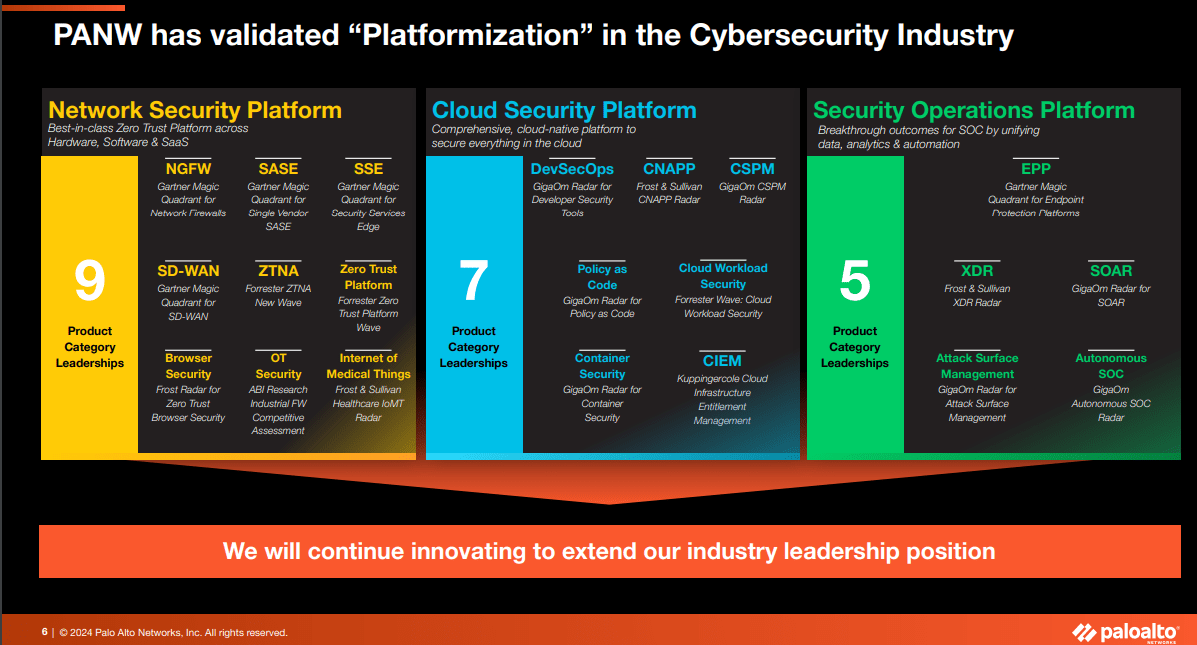
The entire ‘platformization’ strategy, first communicated in the 2Q24 earnings report, entails leveraging the breadth of these three respective platforms, brimming with many BoB (best-of-breed) solutions. The strategy addresses PANW’s issue when it tries to cross-sell to existing customers, who recognize the value of PANW's solutions but are already invested in something similar provided by a competitor. These customers find it hard to justify additional expenditure on PANW's offerings without first achieving a ROI from their initial choice.
In essence, the problem is enterprises have contract duration misalignment across their cybersecurity solutions with multiple different vendors, drastically hampering PANW’s ability to expand its footprint within existing customers and to offer them a unified, holistic platform solution. ‘Platformization’ entails offering the customer the remaining solutions within the respective platform for free until the end of the incumbent’s contract. This relieves the cognitive and financial strain on the customer, and gives PANW ample opportunity to prove they have the superior and most TCO-effective solution by the time a decision must be made as to whether to renew with the incumbent or switch to PANW.
For instance, an enterprise currently using just one or two solutions from PANW’s Cloud Security Platform (e.g., CSPM and Cloud Workload Security), will be offered the opportunity to use all the other solutions in the Cloud Security Platform for free until the contract with incumbents come to an end. It has been indicated that platformization offers will be only for existing customers that have shown a keen interest to expand with PANW, though we wouldn’t be surprised if Arora loosened the criteria to non-existing customers also. Additionally, it seems as though qualifying customers must have only 12-18 months remaining on their incumbent’s contract, as PANW’s management disclosed that this is the timeframe in which they expect notable pressure on their top line, mainly their billings.
In the follow-up article that we will publish next week, we will briefly discuss the merits and potential obstacles of the platformization strategy, and we have already shared detailed views to our subscribers. Though, we want to use most of this article to discuss the networking and network security landscape and how we believe it will evolve from SASE, to SASO (a Convequity term we will explain later), and beyond.
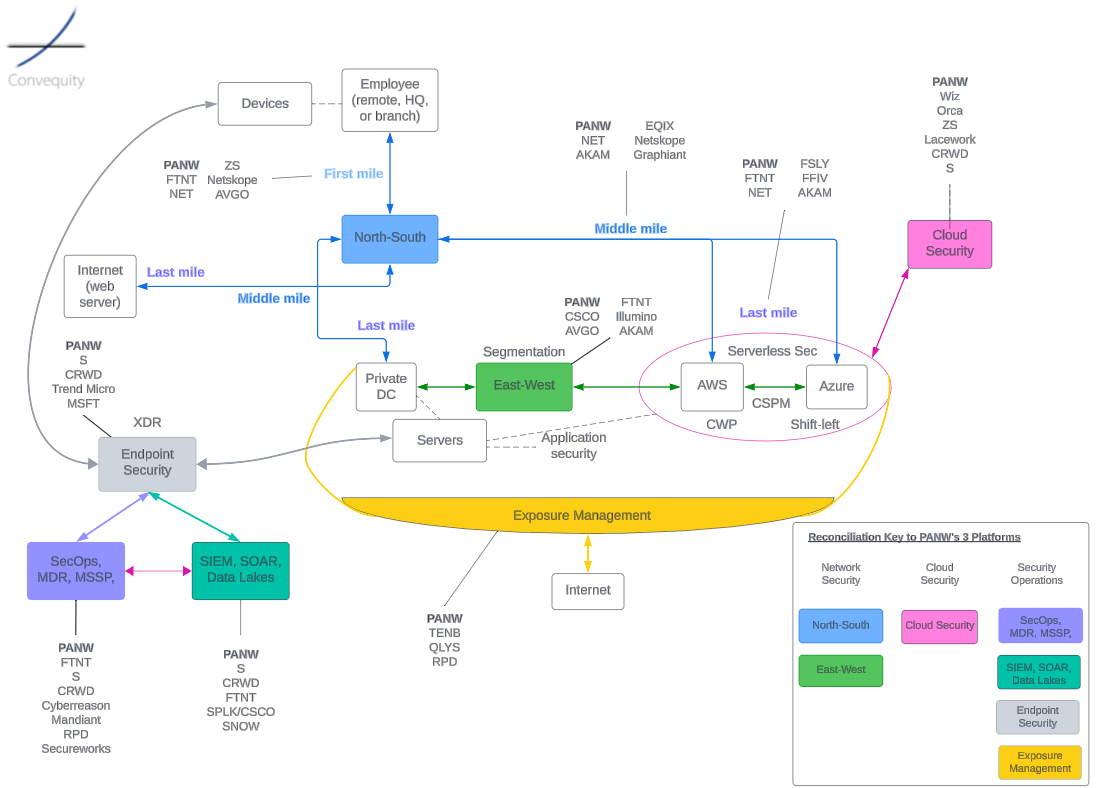
Here is our diagram of the cybersecurity landscape, that is very alternative to what you might have seen elsewhere, as we’re attempting to illustrate how all the areas relate to one another. The reconciliation key in the bottom right corner shows how our labels relate to PANW’s description of its business. We have also indicated the current strongest competitors within each area, breaking out the North-South section into the first, middle, and last mile (which we’ll discuss in the following section). As can be seen, PANW is a strong presence in each area of cybersecurity. It is the North-South area that we will discuss in the remainder of the article, as this is the area in which employees connect to resources (i.e., SASE), and discuss where PANW is currently strong, weak, and where it seems its strategic interests are.
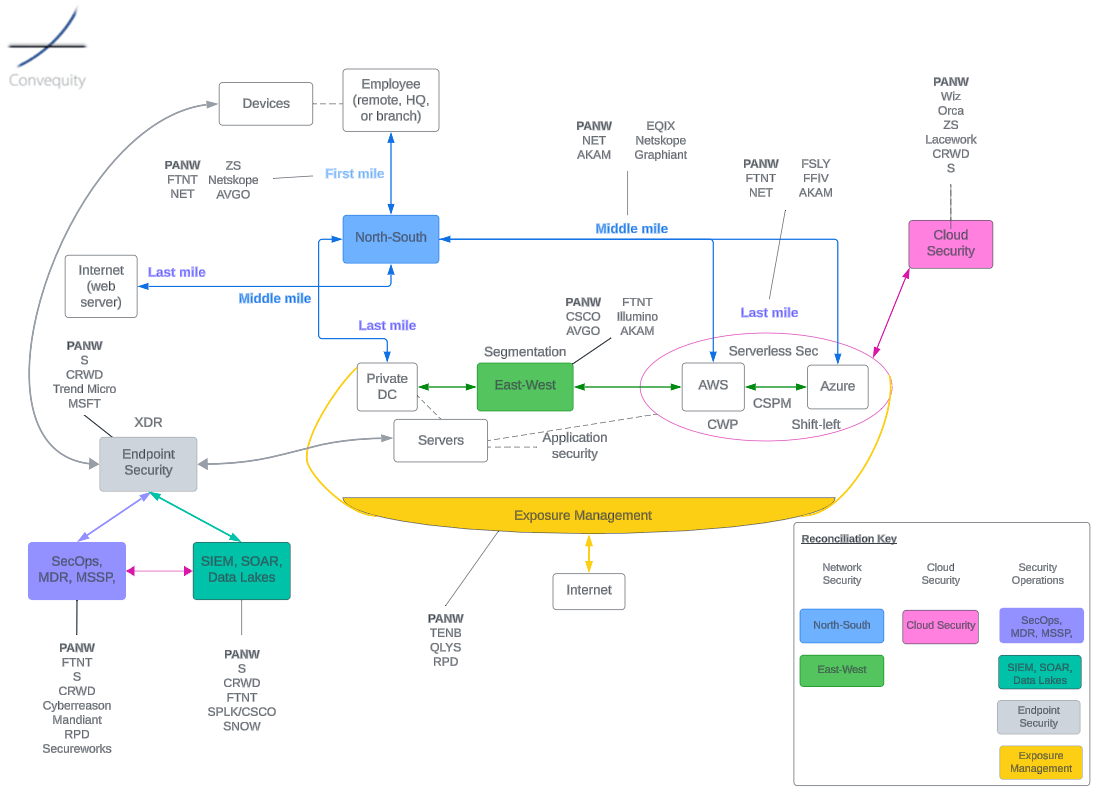
This diagram probably helps understand the industry better if you already have some foundational knowledge. We shall intermittently refer back to this diagram (in this article and the follow-up), though we will lay out the subheadings in this article in alignment with PANW’s three platforms – Network Security, Cloud Security, and Security Operations.
Network Security
We can no longer talk about network security in a vacuum because it is evolving and converging with networking, instigated by Gartner’s unveiling of SASE (Secure Access Service Edge) in 2019 and expedited by the WFH strains put on enterprises during and since the pandemic. Gartner recognized that there had become so many different appliances for conducting various networking and network security functions on-prem, that a better model would be to converge all of these into a PoP (Point of Presence) that is managed by a vendor. The benefits included swapping capex for opex leading to better infrastructure utilization, easier deployments, less costly and more efficient IT management, and greater scalability (e.g., when opening a new office or retail outlet or increasing the size of the workforce). The other major benefit, thrusted into the limelight during COVID-19, was that SASE could process networking and security far more efficiently for remote workers compared to the traditional castle-and-moat networking model.
During 2019-2021, thanks to the assertive leadership and business acumen of Nikesh Arora, PANW quickly emerged as a SASE leader. PANW’s SASE transition and GTM was so successful that they quickly caught up to Zscaler (ZS) who had a notable head start thanks to their prominence in SWG (Secure Web Gateway), which became the most important part of SASE during the pandemic. The primary reason for this is that knowledge workers predominantly use the Internet (even more than SaaS or internal applications). As a result, when workforces transitioned to remote work, it naturally became advantageous to provide them with direct and secure Internet access. ZS offered the most advanced, proven, and recognized cloud-based SWG at the time, leading to a significant number of enterprises flocking to ZS’ SWG, and then expanding to other SASE components.
SASE consists of SSE, which is the SWG, ZTNA, and CASB, and SD-WAN which is a technology for centrally managing an enterprise’s WAN over MPLS and the Internet. And all this, in accordance to Gartner’s definition, must be converged into a single stack in an off-prem PoP (this is different to our definition of converged networking and network security that we call SASO – replacing the ‘Edge’ with ‘Omni’).
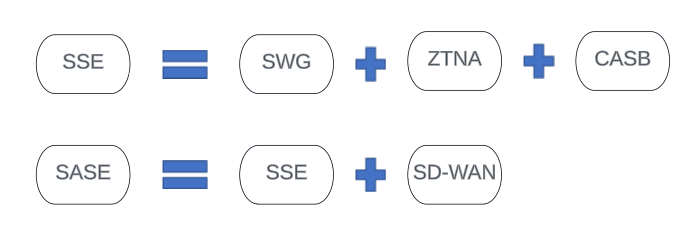
What many people probably don’t know is that PANW, even as a perceived ‘legacy’ firewall vendor back in 2019-21, fundamentally had the SSE components under the hood of their NGFW (Next Generation Firewall).
- PANW’s NGFW was already doing proxy-based inspection, like a SWG does, due to what had become pervasive encryption of network traffic;
- ZTNA is very closely linked to the technology of a firewall and the VPN, in fact, you can do ZTNA with firewall port control functionality (not the only way though);
- And PANW’s NGFW was already the elite in granular application layer (Layer 7 of the OSI reference model) control, making the transition to CASB very natural.
Where Arora stepped in and changed the fortunes for PANW, was with his decision to leverage Google’s global network of PoPs, to catch up to the PoP density of the likes of ZS, Cloudflare (NET), and Netskope. By doing this, PANW only had to set up the software layer at each of Google’s PoPs, enabling them to quickly expand global coverage and close the gap to the others who primarily adopt a colocation PoP strategy (mostly with Equinix) involving infrastructure layer and software layer setups.
This is a classic example for contrasting the differences between PANW and Fortinet (FTNT), as the former (even more so since having Arora at the helm) is more business-oriented, whereas the latter is more engineering-oriented and has the desire to be vertically integrated and build everything from the ground up. In this PoP strategy example, PANW’s business-oriented mindset has propelled them to quickly become the SASE leader, while FTNT’s PoP strategy has meant they have thus far been trailing behind but will probably have the better SASE and wider networking/network security offering over the long term. Having made this comparison, PANW still showed great engineering in making its SASE work on Google’s network, because they managed to achieve tremendous scalability thanks to their process-level engineering capabilities (helped in large part thanks to the influx of former Google talent Arora influenced to join PANW). This is completely contrary to ZS’ Jay Chaudhry’s claims that all PANW and other firewall vendors are doing for SASE is merely ‘moving their DVD player (i.e., firewall) to the PoP and calling it Netflix’ (paraphrased).
The other major move by Arora was buying CloudGenix in 2020, to get the SD-WAN part of SASE. This is another example for comparing PANW and FTNT. PANW’s market-winner mindset acutely understood the GTM implications of adhering to Gartner’s definition of SASE – converged networking and network security must be cloud-delivered, hence why they spent $420m on CloudGenix’s cloud-delivered SD-WAN. This led to leadership recognition by Gartner and contributed to PANW’s great GTM success. FTNT, on the other hand, had long had their own ideology of converged networking/network security, developing SD-WAN inside its NGFW appliance for on-prem requirements, and to some extent they have been stubborn and slow to mold themselves to Gartner’s cloud-delivered definition, at the expense of being dismissed by Gartner and the majority of the SASE market (and investors). However, we believe this perception of FTNT will gradually change over time.
So, when the paradigm is SASE, PANW has the clear upper hand versus FTNT and, along with ZS, is the market leader. However, there is a rich history of markets and industries shifting back and forth between decentralized to centralized architectures, which makes us believe FTNT might win in the long term. For example, telephone networks during ~1880-1990 (centralized) >>> the Internet during 1990s-2000s (decentralized) >>> Web 2.0 2000s-present (centralized). Specifically, within cybersecurity (before SASE) we’ve seen endpoint security such antivirus (a decentralized approach) and network security such as firewalls (a centralized approach) have ups and downs in importance versus the other. In the data ecosystem over the decades, we’ve seen fragmentation (decentralized siloed databases) evolve to consolidation (centralized cloud-based data warehouses) and now there is much discussion about data mesh, a decentralized approach to interacting with data.
With that, our view is that converged networking and network security should not necessarily be conducted strictly by the SASE definition, which is centralized in an off-prem PoP. Instead, it should be conducted wherever it is most economical to do so. This might be on-prem if you are a hybrid enterprise and are using FTNT’s FortiGate, the only on-prem appliance able to do true converged SD-WAN and SSE, i.e., SASE. And as vendors are always striving to tweak out further performance gains and better user experience, we are already seeing players other than FTNT move some of the compute from the PoP to the endpoint – a shift from 100% centralization to some decentralization.
This is why, we will continue to be long-term investors in PANW, but in regards to networking and network security, it is hard to envisage them being a major market winner in, say, 10 years from now. Cloud migration is ongoing but hybrid architectures are also here to stay, meaning SASE isn’t always the best way to process traffic. For example, if an enterprise is using SASE (PANW’s Prisma Access of any other vendors), an employee’s packet needs to be processed for networking and security at two hops – on-prem and in the PoP. The router, and most probably the firewall due to enterprise concerns, would need to process the packet on-prem, and then the packet will be sent to the nearest PoP for the SD-WAN to choose the optimal path and the SSE to do the security inspection and SaaS/Internet access control. Clearly, this adds substantial latency compared to if the entire routing, firewalling, SD-WAN, and SSE can be done in a single stack on-prem. Furthermore, even the SASE stack in the PoP has the SD-WAN and SSE service chained, adding even more latency, because no vendor other FTNT has converged the two sides of SASE into a single stack. FTNT’s advantage here stems from their 20+ year ASIC development.
At this point, we will introduce SASO (Secure Access Service Omni), our version of converged networking and network security. As ‘Omni’ refers to everywhere, SASO means conducting converged networking/security wherever it is most economical, which might be in the PoP, on-prem, or even at a home office. And in reality, most enterprises will need a mix of these converged options because the economy related to transmitting data packets is source-destination dependent, and as enterprises are nowadays with hybrid workforces (remote and office-based) and hybrid IT environments (cloud and on-prem), each packet will have different economics.
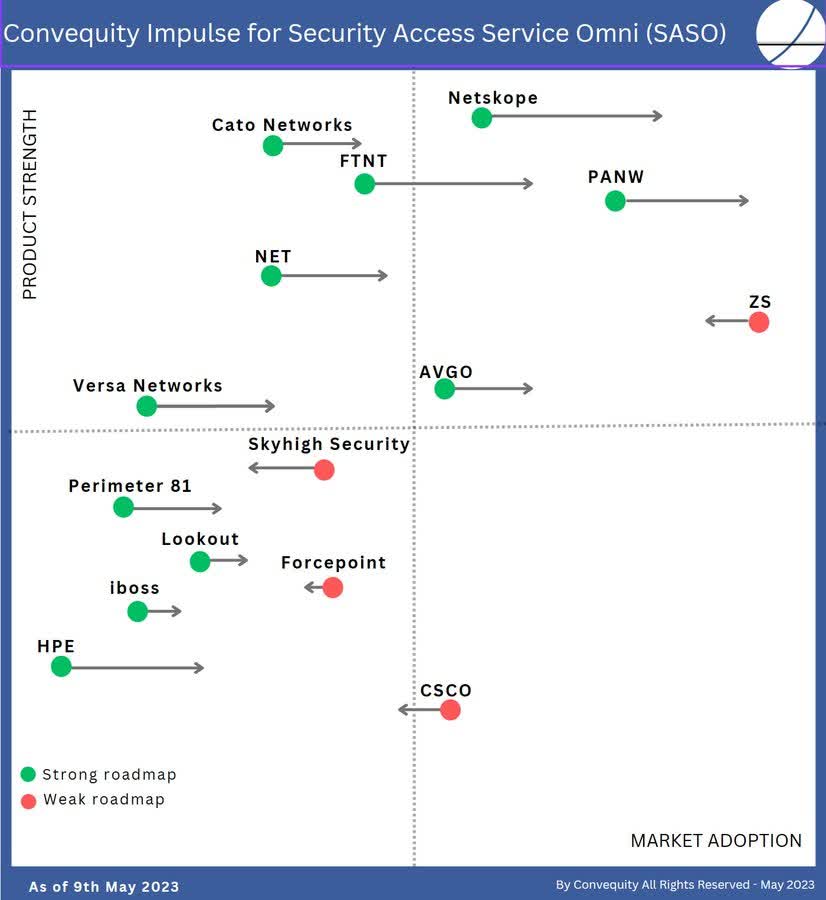
Below we share the Convequity Impulse for SASO – we intend on updating it in a few weeks, making it an annual review. When do the official update, we suspect FTNT will be higher on the Product Strength axis (perhaps the highest), mainly thanks to their multi-pronged global PoP coverage progress, and will have shifted to the right on the Market Adoption axis. PANW will remain high on the Product Strength axis, while probably overtaking ZS on the Market Adoption axis. Netskope will remain either the outright Product Strength leader or a joint leader with FTNT thanks to their global coverage, network performance, in-house SD-WAN and SSE, and a smart endpoint SD-WAN deployment option that addresses some of the latency derived from processing SD-WAN in the PoP. In regards to ZS, we think they could be on the demise because they don’t have in-house SD-WAN, which is a big drawback considering the recent demand trend for single-vendor SASE (that is, a vendor that can provide both SD-WAN and SSE). Actually, ZS did find themselves in a predicament because until recently, they had to partner with SD-WAN vendors, many of which also offer SSE, as there has been substantial market consolidation occurring. To circumvent this precarious situation, ZS has created their own appliance to connect traffic to the nearest ZS PoP, though this isn’t true SD-WAN and ZS venturing into hardware probably isn’t a good idea.
Thus far we’ve discussed SASE and our expectation for the evolution to SASO, but in reality, this is only a portion of the networking and network security landscape. As we pointed out in our previous FTNT article, a good way to view the broader landscape is via the first, middle, and last mile. For convenience, we’ll show the cybersecurity landscape diagram again, to help better envisage these stages that a data packet transits along.
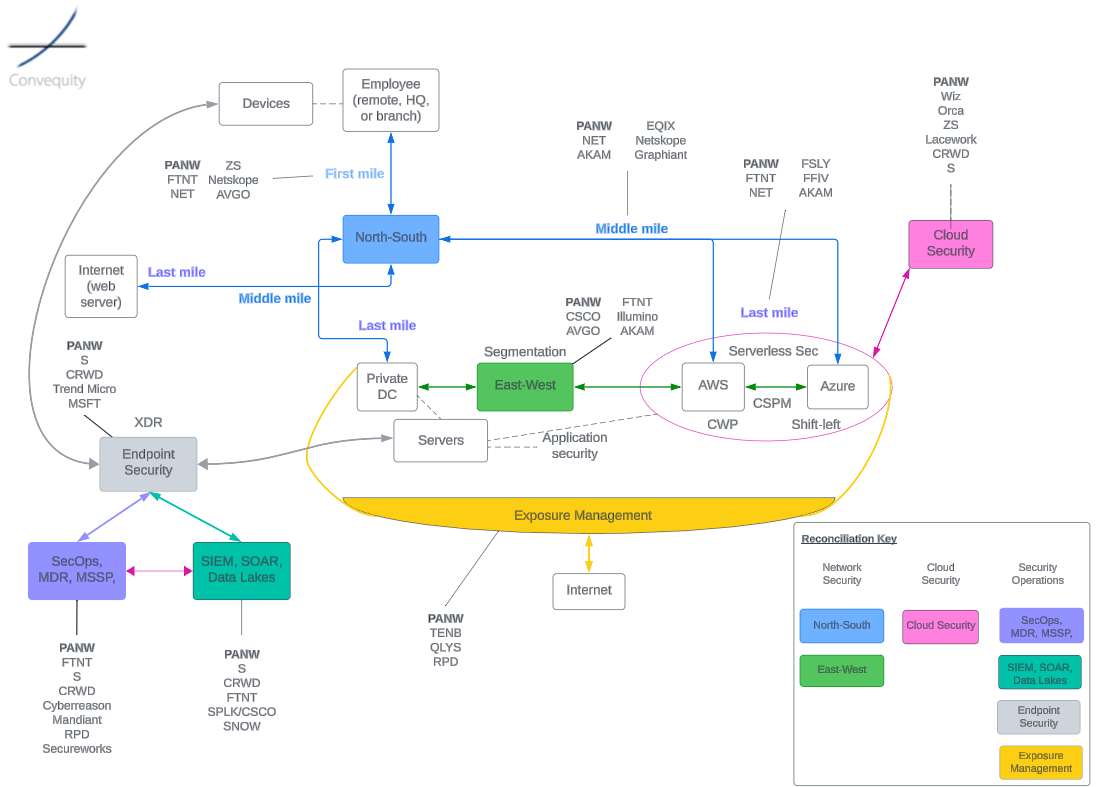
The first mile is essentially where SASE operates – from the employee initiating a request from HQ, a branch, a café, or home, to the PoP, or in the case of SASO, the PoP or the converged on-prem stack (as is available with FTNT). Once the packet has been processed by SD-WAN and SSE, it embarks on the middle mile where it will be transmitted through numerous hops that are part of a web of interlinked networks, aka the Internet. The middle mile is hugely important because it covers the most ground. A poor middle mile for an enterprise will offset any benefits of a well-performing SASE, or first mile. When the packet arrives at the final hop, it takes the last mile journey to its destination, which might be a SaaS application in the cloud, a website server on the Internet, or the employee’s on-prem data center.
While we have recently witnessed consolidation in the first mile, as there has been ample M&A across SD-WAN and SSE vendors, the middle and last mile is still fragmented, ripe for innovation and aggressive expansion strategies. In the next sections we will discuss PANW’s pros and cons within the first, middle, and last mile of networking and network security.
The First Mile: SASE, SASO, or the WAN Edge
The first mile is often referred to as SASE or the WAN Edge, but who knows, maybe our term SASO will also be used in the future (or some variation of it). PANW is solid in the first mile as it has an elite NGFW appliance for on-prem that can do all the SSE functionality. The company is also solid in the PoP-delivered SASE thanks to its dense global coverage (ensuring the nearest PoPs are not too far away) and thanks to having integrated SD-WAN. However, in the realm of SASO, PANW is lagging behind (especially behind FTNT), as the vendor hasn’t integrated SD-WAN into its on-prem NGFW appliance. And this really illuminates where PANW’s strategic interests are. If the company was fully focused on maximizing its future potential in network security, presumably it would have spent the required time to integrate CloudGenix’s SD-WAN knowhow into its NGFW within its Strata platform. We attribute this to either PANW not envisaging the market in the same way FTNT does, or they do see a similar network security vision as FTNT but are too focused on cloud security and SecOps to commit sufficient resources. Hence, as it stands, if/when SASE does evolve to SASO, PANW is not ideally positioned. For an enterprise that uses PANW’s NGFW for SSE on-prem, but they also want SD-WAN, they will need PANW’s PoP to process the heavy lifting aspects of the SD-WAN. In essence, traffic would be processed by the NGFW for the SSE and then move to the PoP for the SD-WAN, creating two hops of heavy-duty processing. Of course, this is not converged networking and security. Moreover, PANW’s disinterest in integrating SD-WAN into Strata means that customers are using multiple panes of glass to manage their PANW stack, whereas FTNT’s carefully planned integrations has enabled true single-pane-of-glass management.
Furthermore, by not having SD-WAN fully integrated in the on-prem stack, PANW inescapably trails behind FTNT in the trend of SD-Branch, short for Software-Defined Branch. As organizations continue to look for ways to reduce the complexity of managing multiple network functions (like routing/SD-WAN, Wi-Fi, security, and WAN optimization) across various locations, SD-Branch offers a unified approach to manage these functions through a single interface. This not only helps in simplifying operations but also in improving overall network performance and security. SD-Branch is not the way to go for all enterprises but will be for a significant portion – i.e., those very hybrid organizations, and FTNT’s deeply integrated and truly unified platform is the ideal solution. This is not only because of integrated on-prem SD-WAN, but also thanks to the integrated switch, Wi-Fi, and other LAN (Local Area Network) technologies that can drastically reduce the IT management strain of using multiple vendors in a single branch. PANW doesn’t have the LAN technologies, which gives us a strong indication that pervasive networking and security is not a top strategic interest. Another note that puts FTNT in a leading position for SD-Branch is that they have compacted the converged networking/security into small and affordable FortiGate appliances. This is ideal for smaller branches, perhaps with 50 or less employees. A stack from PANW or other vendors for SD-Branch purposes would be way too expensive for smaller branches.
Having criticized PANW’s positioning under a possible shift toward some decentralization, on the contrary, they do have impressive client agent capabilities that they use for endpoint security. Similar to how Netskope has developed a smart endpoint agent for managing part of the SD-WAN in a pure software manner, perhaps PANW, with its software agent knowhow, could emulate this and use the endpoint agent to optimize the compute and offload some of the processing from the PoP in order to improve performance and user experience.
So, if network security does somewhat shift its attention from the centralized SASE paradigm to a mix of centralization and decentralization, in the SASO paradigm, PANW would probably be net-net worse off. However, a big bonus for securing PANW’s future SASE dominance is the enterprise browser. Island and Talon, are two Israeli startups that pioneered the enterprise browser, which has the potential to revolutionize network security, and PANW acquired the latter in November 2023 for $625m.
An enterprise browser enables IT admin to centrally set granular policies related to Internet and SaaS access, and by enforcing security as the user initiates connection, it can potentially reduce the need or importance of the main SSE components. For instance, if you can set policies and create lists of approved and disapproved URLs at the browser level, that is, on the user’s endpoint device, then why would you need to do the heavy-duty processing involved with a SWG, whereby the SWG needs to decrypt and the re-encrypt the packets, resulting in unnecessarily high compute costs. The same logic applies to ZTNA and CASB, simply because if you use an enterprise browser to ensure security, in theory you can reduce the number of times the packets need to decrypt and re-encrypt en route to their destination. The packet can be encrypted at the user’s endpoint and decrypted at the destination. In reality, however, the enterprise browser is unlikely to render the other SSE components obsolete because cybersecurity is all about defense and protection in layers. But nonetheless, it is a potential paradigm shift in how network security is conducted, and PANW is front and centre with a BoB solution.
First Mile Competition
We discuss the first mile competition in depth in our subscriber content, so we shall keep it brief here. Apart from FTNT, PANW’s biggest rivalry in the first mile is Broadcom (AVGO), Netskope, NET, Hewlett Packard Enterprise (HPE), and ZS – probably in that order. AVGO, in large part thanks to its M&A, now has the potential to develop a deeply integrated networking and security stack, including its own networking chip, SD-WAN, and SSE – if the company can successfully merge its tech for on- and off-prem it could become a formidable player in SASO and the first mile.
Netskope, NET, and ZS are each strong players with a cloud-delivered approach, though as networking/security evolves, we are already seeing them attempt to adapt with more capable client SASE agents and creating on-prem SD-WAN connectors. This shows that being 100% cloud-delivered in a hybrid world is not feasible.
HPE’s evolution after acquiring Juniper Networks is going to be interesting to watch too. The M&A has substantial overlap that could hamper synergies, although there are substantial market and financial opportunities for HPE to extract from the acquisition.
The Middle Mile: WANaaS
Over the long-term, whoever has the best PoP strategy has the most opportunity across first, middle, and last miles, but specially within the middle mile, which is often referred to as WANaaS (Wide Area Network as-a-Service). Thanks to PANW’s aggressive PoP strategy, leveraging Google’s global network, the company has good coverage, ensuring a not-too-distant first mile, a fairly optimized middle mile, and a very short distance for the last mile. Apart from needing to leverage Google to quickly build up the network to compete against ZS in SASE during 2019-21, PANW justified the approach with the contentment that Google (along with AWS) has the densest global private backbone for delivering the best possible transit. Furthermore, as most traffic is cloud-bound for most enterprises, it makes even more sense to use Google’s PoPs.
The problem is this makes PANW’s Prisma SASE more expensive for customers, because the customer needs to pay both PANW’s and Google’s gross margins. Let’s estimate that Google’s gross margin for selling IaaS to PANW is 40% (assuming PANW has a good deal) and Prisma SASE has a gross margin of 80%, then for $1 of raw transit/processing costs the customer will be actually paying $8.33 ($1 / (1 – 40%) / (1 – 80%) = $8.33). Let’s contrast this to FTNT who has a four-pronged PoP strategy but its primary long-term PoP focus is to buy or build its own or co-build with service providers. Under this strategy, FTNT customers won’t need to pay a gross margin to a hyperscaler or colocation provider, then will just pay FTNT’s gross margin. For example, if FortiSASE has a gross margin of 80%, then for $1 of raw transit/processing costs, the customer will only pay $5 ($1 / (1-80%) = $5). Though, in reality FTNT’s raw COGS are going to be lower thanks to their ASIC chips that are going to be deployed at their PoPs. This means, for example, where PANW can deliver X amount of raw transit/processing costs for $1, FTNT could deliver the same amount for $0.50 or even lower, thus offering the vendor more scope to match PANW’s gross margin while also having lower COGS and being even more affordable for customers.
The other issue with PANW using Google’s PoPs for SASE is that oftentimes the first mile PoP is not the PoP that conducts the heavy-duty SSE processing. This is because some of Google’s PoPs are smaller and not equipped to deliver heavy-duty processing. Instead, such PoPs are just there as an entry point to the Google network, and they will route the packets to the nearest PoP that is equipped with the infrastructure to do the heavy lifting. Clearly, for PANW’s SASE customers this will add latency, which may not be very noticeable now, but relatively speaking, when other vendors’ have fully executed their colocation or proprietary PoP strategies, this could be a notable drawback.
Middle Mile Competition
Despite being mature, this is a very fragmented area of networking and security. Though, in a similar vein to how the first mile has consolidated as vendors originating in both networking and network security made a beeline for SASE, resulting in considerable M&A, the middle mile may experience the same. Right now, the middle mile consists of players from SASE, Network-as-a-Service (NaaS) vendors, ISPs, hyperscalers, and CDNs. The players that have greater control of the PoPs’ hardware, infrastructure, and the software/hardware integration, are the ones with the most opportunity to create additional value, via lower costs and better performance. The middle mile is certainly more about networking than network security, and as this is not in PANW’s gene, they are unlikely to be the aggressor in this space. With respect to SASE names, NET, Netskope, and FTNT looks the strongest, with the latter being the one who creates the most incremental value going forward.
The Last Mile: Application Edge
The last mile is from the final PoP to where the application resides, which may be in the cloud or on-prem - and the application in an enterprise’s premises could be a web server in a DMZ zone for Internet consumers, or it could be an internal application for employees. Like FTNT, PANW is very strong here. They have software-based NGFWs ideal for the entrance to an enterprise’s cloud environment, and of course, their BoB on-prem NGFW in software or appliance form factor to screen the last mile traffic. Compared to FTNT, however, they do lack some on-prem solutions that protect applications, such as WAF (Web Application Firewall), DDoS protection, and bot protection. Though, PANW has more solutions than FTNT, many of which are considered BoB, for cloud-native application protection. And again, this comparison illuminates where PANW’s strategic interests are – they are very much cloud focused, which has completely turned around the company’s fortunes in the past few years, but could be somewhat of an impingement if on-prem regains importance.
Last Mile Competition
PANW is probably behind NET as the number on last mile player for applications in the cloud. When it comes to hybrid requirements, FTNT also enters the conversation. Other CDN names, especially Fastly (FSLY), has great prospects in the last mile as they are building a comprehensive platform for applications, from development, to compute, to networking, to security, and to observability.
The Entire Networking + Network Security Convergence
As it stands, PANW is too software-focused to emerge as one of the key victors in this broad and deep area of networking and network security. They will continue to be a SASE leader and gain market share within the first mile, even in the evolution to SASO, because they are simply the best at security, on-prem or in PoP. But for hybrid enterprises and/or enterprises with specific needs, PANW is way less flexible than FTNT. The last mile is also a stronghold for PANW. The middle mile is where PANW may lose some relevancy, because there are alternative players that can potentially deliver better user experience and lower costs.
Financials & Valuation
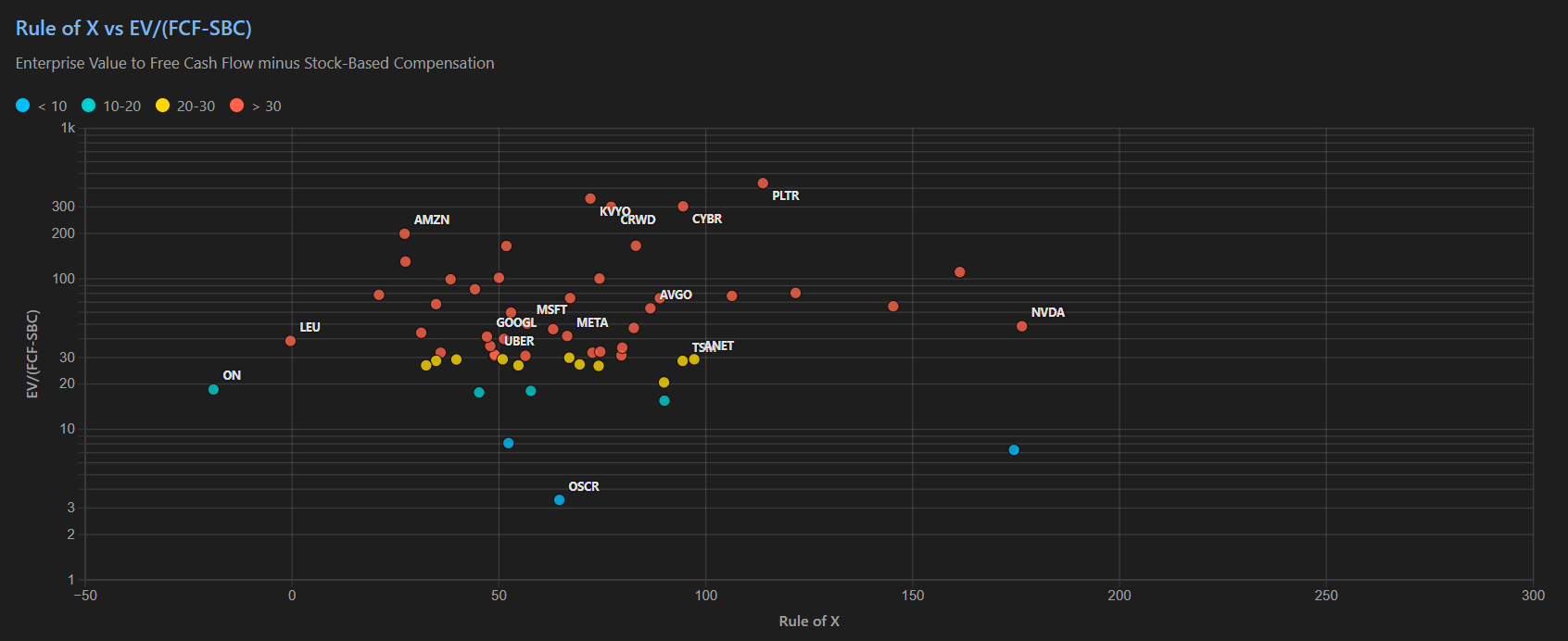
Recently, we've replaced our Rule of 40 analysis with a variant, the Rule of X. Bessemer Ventures introduced the metric in late 2023, after observing that statistically speaking, growth has a greater correlation with investor returns than FCF margin. To incorporate the notion of growth having greater influence on returns, Bessemer Ventures recommends applying a multiplier to the NTM growth that is part of the Rule of 40. They state that the multiplier for public companies is mostly from 2x-3x, with 2.3x being the median. We've adapted the Rule of X to incorporate SBC percentage, resulting in the following formula: Rule of X (inc. SBC) = NTM growth * 2.3 + (FCF margin - SBC %)
The table below shows a list of 41 stocks across our coverage remit of cybersecurity, data, productivity, and observability, ranked by the Rule of X (inc. SBC). Our analysis then extends to cross referencing the Rule of X with relative valuations, DCF valuation discounts, and price changes. As you might infer, this is somewhat contrarian analysis, attempting to identify stocks out-of-favour but with stellar financial performance, as indicated by the Rule of X. In essence, if you can find a stock with a dark, medium, or light green Rule of X followed by green valuations, the stock looks attractive. The bonus is if there are green prices changes too; however, given the market exuberance of late, this is unlikely. Therefore, an amber price change - meaning a relatively small change - is probably the best price change to align with green Rule of X and green valuations.
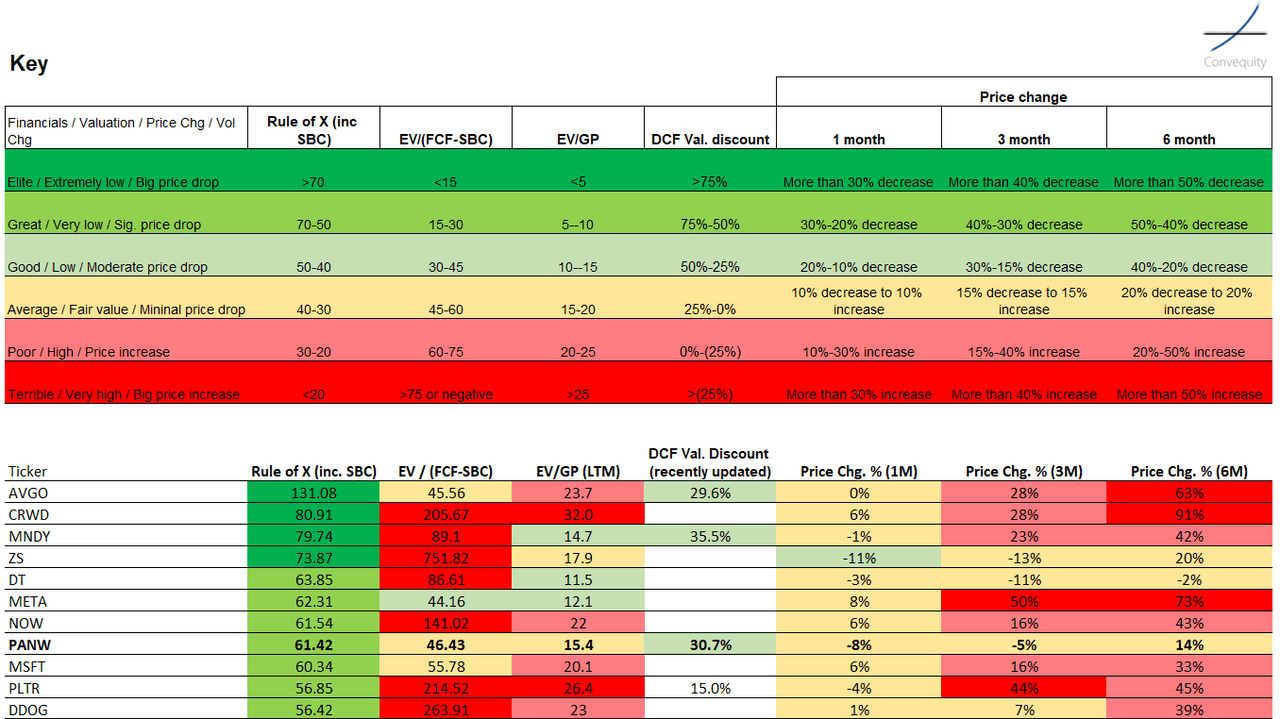
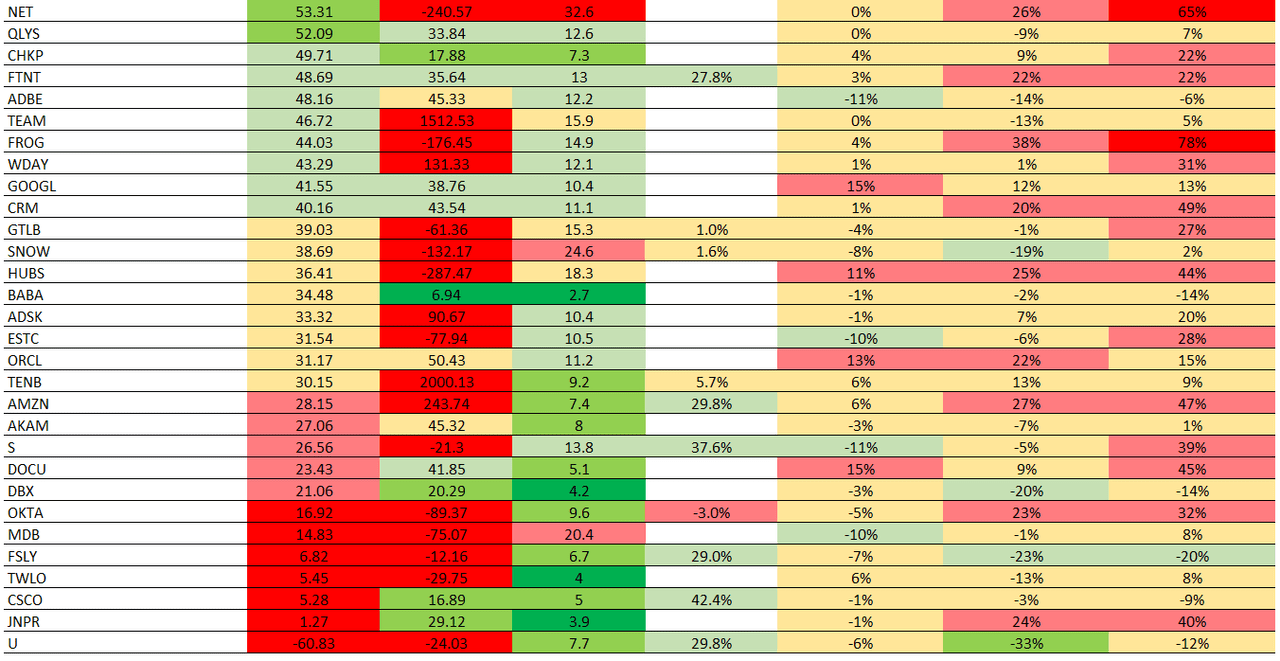
Based on this analysis, we think that PANW is still worth holding, especially since the recent price retreat following doubts around the platformization strategy. The company has a stellar Rule of X thanks to mid-teen NTM growth expectations, a very high TTM FCF margin of high-30s, and a TTM SBC percentage of 14%, which has rapidly declined in recent quarters. And the valuation from a relative perspective is still not extreme, dependent, however, on what type of investment style you apply. And our latest DCF valuation suggests ~30% upside thanks to the recent drawdown.
Arora is confident that they can sustain mid-30s FCF margin, despite billings temporarily contributing less over the next 12 months due to the platformization strategy, thanks to the scope the company has in reducing opex. And following the initial 12-18 months of the platformization strategy, whereby PANW is basically allowing all of its customers to use significant portions of their platforms for free, Arora expects growth to reaccelerate. We will briefly discuss the merits and potential drawbacks of the platformization strategy in a follow-up report, though Arora's growth forecast is plausible, as well as the FCF margin sustainability, meaning we think PANW's Rule of X (inc. SBC) will not deteriorate, which will be important for the price/valuation gap to close. For a deeper discussion on PANW versus its competitors and the platformization strategy, check out our subscriber-only content.
Here is the DCF valuation for PANW, exclusive for Premium Convequity subscribers (not shared in the free article). You can change the key parameters: the long-term/terminal FCF margin, the SBC inclusion option, the long-term/SBC %, the FY25-FY29 CAGR, and the number of years to reach intrinsic value.
Risks
Business
There are substantial business risks for PANW, as it relates to what we've covered in this article, as well as the platformization strategy. As investors, we are concerned that PANW doesn't have the focus that FTNT has on the likely evolution of networking and network security. PANW is already experiencing a decline in appliance revenue (note: PANW reports product growth but this includes not only appliances but also software-based firewalls and associated subscriptions, both of which are growing well for the segment) while FTNT's appliance revenue, except for the recent decline due to the aftermath of supply-chain disruption over buying, is still on a growth trajectory. This is pretty telling as it strongly indicates FTNT is more suitable for hybrid environments, and FTNT's strength in hybrid will only get stronger as the attention branches out from SASE, to SASO, and then the broader landscape.
In essence, PANW's focus in networking and security is software-based, which provides great flexibility, but they cannot compete with an integrated hardware/software appliance with custom ASICs when it comes to performance. And ultimately, as more attention is placed on the convergence and consolidation of the first, middle, and last miles, performance is going to be front and centre.
We will share more thoughts on platformization in the follow-up article, though the key risk is that a notable portion of customers decide not to switch to PANW following the estimated 12-18 month period of free services. The most likely reason for this would be because the incumbent has offered them a huge discount that they can't turn down. In response, PANW may then need to offer a huge discount after already providing free services for ~12-18 months, which would be a huge hit to the top and bottom lines and very disappointing for investors.
Macro
Our macro view on PANW is very similar to what it is on FTNT, shared in our previous article. PANW's product diversity will help mitigate an economic deterioration and further tightening of budgets. Though, compared to FTNT, an added macro risk is that PANW has less geographic diversification, meaning they don't have as much to offset a decline in its key North American market. A big positive, however, is PANW's very high FCF margin that would be very attractive to investors if we did experience a harsh economic downturn.
Conclusion
PANW is a great cybersecurity company with a great leader who is making bold but necessary bets to continue generating shareholder value amid a very tough cybersecurity industry. As investors, we are somewhat disappointed not to see PANW more focused and visionary within the networking and security landscape. From our past observations, simply and blindly following Gartner's market and technology ideologies is not good for long-term differentiation and competitiveness. Typically, PANW leads the way rather than follow, especially in cloud security and SecOps and back during the 2010s with its NGFW, but right now it seems to be following in network security, which is a source of frustration to us.
Nonetheless, any demise in their core business will be very elongated and gradual, and the higher growth opportunities are indeed in cloud security and SecOps. With that, and the attractive financials, the not-too-expensive valuations, and the recent price decline, we're still holding on to PANW and intend to be long-term investors, ready to buy on any sharp correction.