Themes: SD-WAN & SASE Industry Review 2024 (Pt.1)

Summary
- SASE is not a universal solution for all networking and security needs. In Part 1 we explain SASE's limited scope within the larger realm of secure networking.
- The landscape of distributed cloud networking includes WAN Edge, WAN Middle Mile, and Cloud/Application Edge categories, each with its own technologies and solutions.
- The integration of SD-WAN with SASE is driving more adoption of SD-WAN, and vendors that can offer integrated solutions with a focus on networking performance, security, and cost-effectiveness are better positioned in the market.
Companies covered: PANW, FTNT, ZS, CSCO, HPE, JNPR, MSFT, NET, Netskope, Cato Networks, Versa Networks, VMW (AVGO), Alkira, Island, Talon, EQIX.
In the early part of this year, we published a comprehensive guide on the subject of Secure Access Service OMNI (SASO), which is Convequity's modified version of Gartner's SASE, rooted in the long-term premise that:
- Secure Service Edge (SSE) alone does not fully meet the evolving needs of customers, especially those transitioning back to office environments or adopting hybrid work models.
- Sole reliance on Software-Defined Wide Area Networking (SD-WAN) is inadequate, as it becomes increasingly clear that network and security functions are converging.
Moreover, we addressed a critical point in the existing Secure Access Service Edge (SASE) framework. Traditional SASE models often overlook or undervalue the importance of hybrid deployment strategies, an oversight that is misaligned with the practical needs and perspectives of end users.
To encapsulate our perspective on what we believe to be the next evolutionary phase of SASE — itself an advancement from SSE and SD-WAN in the realms of security and networking — we introduced the "Convequity Pulse" graph to showcase our SASO evaluations. Here, we reimagined the "Edge" component of SASE, replacing it with "Omni" in SASO (Secure Access Service Omni). This shift emphasizes our viewpoint that security and networking functions need not be confined to the server edge or cloud Points of Presence (PoPs). Instead, these functions can be effectively deployed on-premises, or at the premises of customers or service providers.
Lately, the concept has gained traction in the industry, with some vendors referring to it as "universal SASE," "hybrid SASE," or "private SASE." These terminologies, while varied, stem from a common foundational concept.
Since the release of our last guide, the market landscape has witnessed significant shifts. Notably, Gartner expedited the release of its single-vendor SASE Magic Quadrant (MQ) and updated its SD-WAN MQ. Concurrently, Forrester revised its Zero Trust Edge (ZTE) wave report. In this three-part series, we will offer our latest thoughts on the industry.
SASE doesn't cover all parts of networking & security
As we delve into the concept of SASE, it's crucial to establish a foundational understanding for our readers: SASE is not a panacea for all networking and security challenges faced by organizations. It should not be mistaken as a universal solution or a 'Swiss Army knife' capable of addressing every networking and security need for all companies.
Our analysis reveals several key insights in this context:
- Convergence of Networking and Security: We are observing a trend where networking is increasingly merging with network security. It's becoming commonplace for networking teams to either merge with network security teams or to collaborate closely, particularly in procurement decisions.
- Persistence of On-Premises Infrastructure: Despite the rise of cloud-based solutions, the traditional on-prem technology stack remains relevant and necessary. For example, routers within most enterprises cannot be entirely eliminated. Without them, individual devices would need to establish Internet connections independently, either through cellular networks or virtual routers.
- Limitations of SASE in Addressing All Needs: SASE primarily focuses on user networking and security. However, it's important to note that it does not comprehensively address networking and security for applications or workloads. This segment of the market, which is significant yet not fully hyped, remains largely unaddressed by SASE.
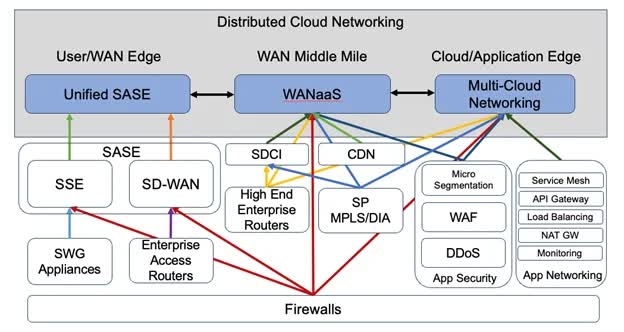
To provide a more structured understanding of the future landscape of networking and security, we refer to Dell'Oro's comprehensive taxonomy chart. This chart categorizes key technologies within what Dell'Oro terms 'distributed cloud networking.'
In this framework, Dell'Oro identifies three overarching categories:
- WAN Edge: This involves technologies and solutions focused on the edge of the Wide Area Network, playing a crucial role in connecting different network segments.
- WAN Middle Mile: This category includes technologies that manage and optimize the connections and data flow between different WAN edges.
- Cloud/Application Edge: This refers to the technologies that are specifically tailored for application-level networking and security, encompassing solutions that directly impact application performance and security.
To gain a more intuitive understanding of how a user interacts with a SaaS application, and how this relates to the various aspects of networking and security, consider the following step-by-step process:
- Device Utilization: The user operates either a managed device (Corporate-Owned, Personally Enabled, COPE) or a personal device (Bring Your Own Device, BYOD).
- Endpoint Security: The device is protected by endpoint security software from companies like Microsoft (MSFT), CrowdStrike (CRWD), Symantec (S), Broadcom (AVGO), etc. Additionally, network security vendors’ software is also installed, including solutions from Zscaler (ZS), Palo Alto Networks (PANW), Fortinet (FTNT), Cisco Systems (CSCO), Check Point Software Technologies (CHKP), and Netskope.
- Browser Access: The user accesses the application through a browser, which could be a regular browser, a Remote Browser Isolation (RBI) system, or a secured browser provided by companies like Island or Talon (recently acquired by PANW).
- Application Access: The user inputs the URL of the SaaS application in the browser and initiates the connection.
- Routing and Firewall Security (WAN Edge): The data packet is sent to the router, passes through firewall security checks, and is dispatched over the Internet. For remote users, the traffic might be rerouted through the corporate network via VPN or, if using SSE, sent directly to a cloud PoP where routing and firewalling occur before the packet is dispatched.
- Transit (Middle Mile): After leaving the router, the packet undergoes various transit stages, analogous to a physical parcel delivery system, involving multiple hops and network operators.
- Destination (Cloud/Application Edge): The packet eventually reaches the SaaS application's server, located either in the cloud or on a provider's server. Here, the server authenticates the user's identity before processing the request.
- Server-side Security: Authentication may occur on one server, while the actual application server may reside on a different server, possibly in another cloud or on-premises environment.
Breaking this down further:
- Points 1-4: These primarily fall under endpoint security, focusing on securing the endpoint device and its software environment.
- Point 5: Represents the WAN Edge, which is the initial part of WAN transport, involving routing and firewall security.
- Point 6: Constitutes the Middle Mile of the WAN, where the packet is transferred and dispatched by multiple network operators.
- Point 7: This is the Cloud/Application Edge, where the packet reaches its destination and responds to the user's requests.
- Point 8: Involves security for cloud applications, known as Cloud-Native Application Protection Platform (CNAPP) or an evolved form of endpoint security tailored for cloud environments.
In analyzing the landscape of SASE and its role within the broader context of distributed cloud networking, several key points emerge:




