Cloud Security Series #5: Pre-IPO, Aqua Security
Summary
- Aqua Security is the 5th name we've deeply covered in the thriving cloud security market.
- Aqua has a very broad platform but there are question marks over its quality versus Palo Alto Network's Prisma Cloud.
- Whereas Wiz and Orca are significant rivals to Prisma Cloud's future dominance, we consider Aqua a second tier CNAPP vendor.
- Nonetheless, for those interested in Palo Alto Networks and gaining a better understanding of its high growth cloud security market, this report will be a useful read.
- Next we're going to return our attention to SentinelOne, as they are also emerging as a key cloud security name. This will be published in a few days.

TU IS/iStock via Getty Images
Overview
Year founded: 2015
Headquarters: Israel
Company status: Private
Estimated TTM revenue: c. $45m
Market: Cloud security >>> CNAPP (Cloud Security Application Protection Platform)
Key competitors: Prisma Cloud (Palo Alto Networks), Wiz, Orca Security, Lacework, Sysdig
Estimated number of employees: 300
Business model: SaaS and on-prem >>> open-source engagement
Executive Summary
Aqua Security is a private company founded in 2015 and started out under the name of Scalock. In the beginning its primary service was scanning container images for vulnerabilities and deviations from custom policies, benchmark standards, and best practices. The company soon changed its name to Aqua Security, and also expanded capabilities within the container scanning domain – scanning images in repositories and those integrated into the CI/CD pipeline.
In recent years, Aqua has branched out along the two dimensions encapsulating the CNAPP market, that we’ve depicted in the recent Wiz and Prisma Cloud reports – the security spectrum and the abstraction spectrum. They’ve extended out from static container image vulnerability scanning toward the shift-left and shift-right ends of the security spectrum, and in doing so they've transformed from a pure agentless vendor to an agentless + agent-based vendor. Additionally, they've also branched out from containers into serverless and VMs along the abstraction spectrum. This is illustrated in the following diagram, where we compared Aqua to Prisma Cloud.
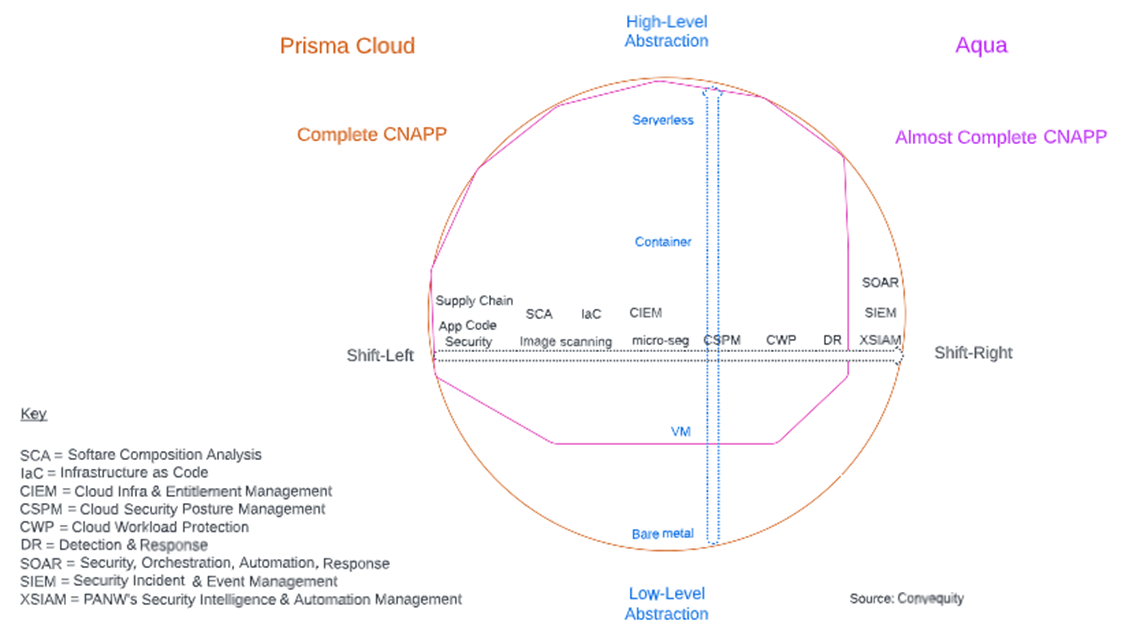
Thanks to these expansion efforts, Aqua can now provide security across the full application lifecycle (from development to production), throughout the whole stack (infra, hosts, OS, workloads, orchestration platforms, and cloud services layers), for VMs, containers, and serverless functions.
Aqua’s platform breadth is a key advantage for them as a main objective for many orgs is vendor consolidation. However, in this report we do raise concerns regarding Aqua’s effectiveness in runtime security, aka CWP as labelled in the diagram, as well as the quality within its platform breadth. As we’ve explained in recent cloud security reports, as shift-left and shift-right focused security has received more attention, it appears that real-time runtime security has become less of a priority for now. But, as cloud security matures, we expect real-time runtime security to return as a top priority, at which point Aqua may lose some competitiveness, especially against the CWP leaders such as PANW, S, and CRWD, which come from EDR origins and thus can provide greater contextual endpoint knowhow.
Another point we’ll make, is that as the trilemma, which we’ve presented in prior reports, indicates that enterprises are opting for ease of deployment (often in the wake of the pandemic as enterprises quickly shifted more ops to the cloud and urgently needed compliance assistance) and comprehensiveness over timeliness, there seems to be less demand for agent deployments (and this is likely the primary cause for Lacework’s woes in 2022) which are a necessity for real-time runtime protection. Deploying and maintaining agents is also resource intensive, therefore, the many orgs tightening their budgets is likely another reason for less agent and real-time security demand.
With these thoughts in mind, Aqua’s inferiority in regards to runtime security might not be a major impediment to business success at present. Although, if we are correct in predicting that real-time runtime security will eventually return as a top priority once cloud security has moved along the maturity curve and the economy recovers, then Aqua may be at a disadvantage – and this may occur in the not-too-distant future.
In October 2022, Aqua announced that they doubled revenues during the preceding 18 months, which is testament that they’ve succeeded in riding the cloud security wave in the advent of COVID-19. Despite the recent success, as we’ll discuss later in the report, we do have concerns regarding Aqua’s GTM and sales leadership. From a particular inside source, we know that about six months ago Aqua’s revenue was about $36m. If you work backwards from this point, estimates for revenue in 2020 would be in the $10m to $20m range. From one perspective this looks impressive, but on the other hand it could be argued that the GTM execution has been poor considering that Aqua was one of the first pure-play container security startups in a high-growth market. From 2020, Prisma Cloud probably had a revenue base that was 20x higher than Aqua's and still managed to grow much faster - this adds some perspective to Aqua's relatively poor GTM.
Nonetheless, having developed core expertise in containers, considered the heart of modern application architectures, Aqua has positioned itself optimally to expand across the CNAPP landscape to be a respected competitor.
Key Leaders
Amir Jerbi
Aqua was founded in Israel in 2015, by Amir Jerbi, the CTO, and Dror Davidoff, the CEO. As has been the beginnings of numerous Israeli security startup founders, in 1995 Jerbi began his professional career working for the IDF (Israeli Defense Force). Within the IDF, he worked for the Mamram division which is responsible for the IDF’s computer and network systems and creating the military’s closed intranet network. In 2000, Jerbi moved to computer systems (mainframes) giant, CA Technologies, where he spent the next 15 years primarily working on the development of access control products. During this time, he progressed from being a developer, to a team leader, an architect, a lead architect, and finally to the chief architect for CA’s access control product, which put him in charge of the overall architectural design. In February 2015, Jerbi left CA and founded Aqua.




