Themes: OT Security Series (Pt.3) - Tenable

Summary
- Part 3 of the OT Security Series doubles up as an initiating report on Tenable.
- Tenable hasn't attracted much investor interest over the past few years, despite the company making strategic moves. In this report, we consider what is different today.
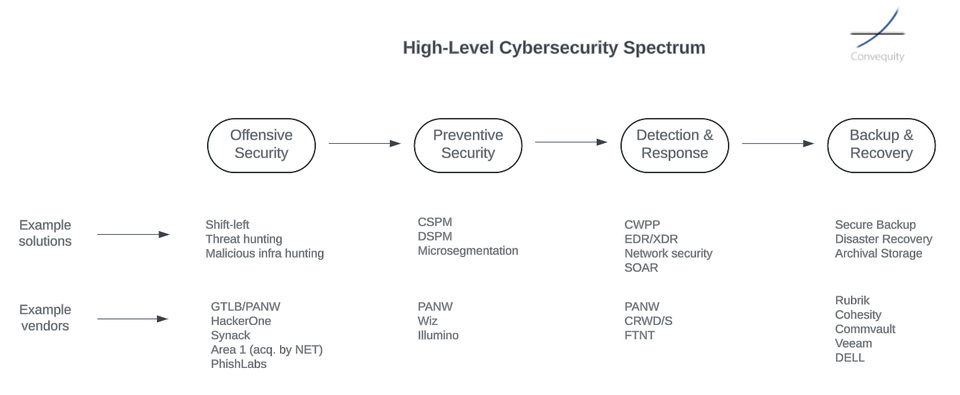
- Tenable is a very capable underdog in the OT security market, and is shining in the most sought after areas, Visibility and Hygiene, in reference to the Convequity OT Roadmap.
- In Part 3, we provide an update of the OT security landscape, dive into Tenable's business, products, and architecture, evaluate its OT security prospects, and then discuss investment considerations.
- The the key question for Tenable's bull thesis is whether Tenable can move its status from a Tier 2 to a BoB vendor (in OT & cloud) while improving its margins - this is what we aim to answer.
OT Security Market Development
For many years, dating back to the early 2010s, the OT security market has failed to sustain strong momentum. There have been periods when it has been hyped, and then periods when the market lost its buzz. COVID-19 certainly triggered a hype period for OT security. The crisis reinvigorated the long horizon concept of Industry 4.0 and the need for greater digitalization and connectivity of industrial processes. However, as industrial and less modernized verticals and companies pursued digital transformation, ransomware gangs exploited their expanded attack surface and weakening security posture. This led to significantly more interest in OT security during the early 2021 through 2023 period.
One way to discern the level of hype is by observing the likes of ZS and CRWD making a marketing beeline for OT security, making exaggerated claims of having a comprehensive OT security suite. Though, from some perspectives it seems as though the buzz toward OT security has simmered down somewhat, which is indicative by FTNT and PANW both not mentioning OT security in their most recent earnings calls. Furthermore, ZS has only briefly mentioned OT security, without diving into any details, signaling that OT security momentum may have paused.
The temporary slowdown (if that is indeed the case), is attributed to the ongoing budget cuts and careful spending among SMBs and enterprises. In the trend of vendor consolidation, enterprises may be cutting corners and taking the risk in repurposing existing IT security solutions to protect OT assets. This, of course, would be short-term fixes, because, as stated in previous OT Security Series reports, OT has different security and operational requirements than IT. Moreover, the ransomware attacks on OT-heavy verticals remains at elevated levels, not helped by the rising number of CVEs (Common Vulnerability & Exposures) as enterprises provision increasingly more IIoT and connected OT as they continue their digital transformation. Here are some notable events of cybercrime, mostly ransomware, against governments and enterprises during 2023 so far.
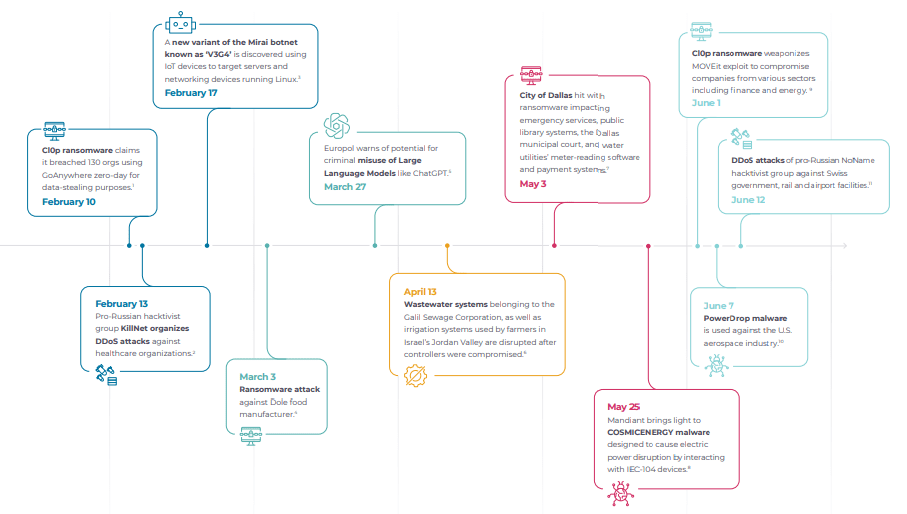
Due to the rise in the number of IoT devices, there are now more CVEs present in IoT/OT than in IT environments. This is one factor driving the elevated ransomware activity. Throughout 2023, the CIOp ransomware gang has been claiming on average 14 new victims per day, including US government agencies, oil & gas companies, and healthcare organizations, mostly by exploiting a CVE in the MOVEit software, which is an enterprise-scale file transfer service. The LockBit Group join CIOp as the most prolific ransomware gang at present, extorting $91m from the US alone in 2023. LockBit is a RaaS (Ransomware-as-a-Service) group, an approach to ransomware attacks that we first discussed back in June 2021, whereby sophisticated cybercriminals create ransomware packages with attack instructions included, and then submit these to less capable or even amateur cybercriminals, and split the ensuing profits. Just like SaaS, RaaS is highly scalable, so much so, that it is estimated that LockBit is responsible for 10% to 25% of all ransomware attacks, dependent on the country.
The following chart shows that the trailing average of monthly new ransomware victims has substantially increased in 2023. October 2023 was an unusual month of lower ransomware activity, that may be attributed to notable law enforcement successes toward the end of August. During this time period, the FBI disrupted the Qakbot ransomware group's infrastructure and remediated infected devices. In a similar vein, the Ragnar Locker ransomware online presence was eliminated in a coordinated international effort. Around the same time, Ukrainian hackers claimed to have erased the server data of the Trigona ransomware group, purportedly linked to Russia. However, it is highly probable that these gangs will soon reorganize themselves and resume the attacks.