Follow-Ups: Fortinet – Multiple Secular Tailwinds & Significant Relative Mispricing
Executive Summary
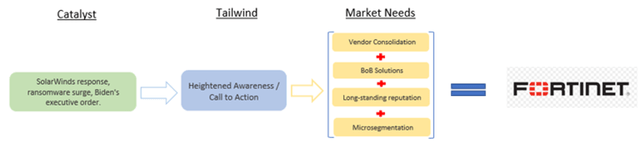
FTNT is benefitting from multiple secular tailwinds – general heightened cybercrime awareness and calls to action, hybrid developments, the connectivity evolution, and OT security needs. FTNT’s ability to fortify company-wide security amid distributed infrastructures, enhance productivity, deliver the highest security ROI, provide solution consolidation, and its long-standing exemplary reputation, is making it a prime beneficiary of these secular trends.
In addition to the top-down investment case, there is a significant relative mispricing reflecting a large discrepancy between FTNT’s quality and the market’s perception. Moreover, the DCF also indicates a 20%-30% discount to intrinsic value. Given the tailwinds, the business quality, the valuation considerations, and the share buyback program [recently increased by $1.25bn], we’re still long-term bullish and will be happy to add more shares on corrections.
Figure 1 - Top-Down Investment Case for FTNT
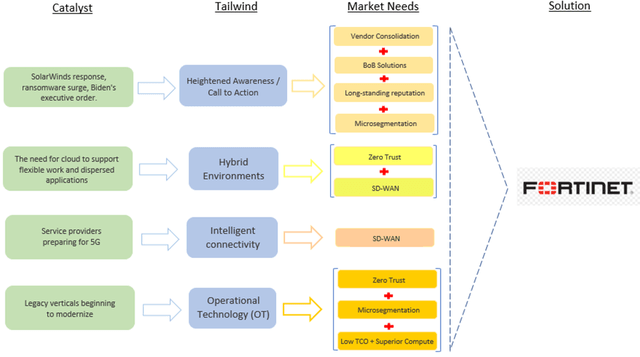
Source: Convequity
Heightened Awareness & Call to Action
SolarWinds Response
The SolarWinds data breach unveiled in December 2020, was an historic point in cybersecurity that generated a new wave of awareness [and cybercrime] across the corporate world. It highlighted the growing sophistication of bad actors, that we discussed in Why We Believe SentinelOne is Better than Crowdstrike [the paragraph after Figure 9], and emphasized the need to reassess security defenses and overall security posture.
In the ATI exclusive, Palo Alto Networks: Significant Mispricing, we published in April 2021, we postulated a typical corporate timeline for a full response to the SolarWinds attack [the malware is actually called Sunburst]. We anticipated that vendors, especially broad-based platform vendors like PANW and FTNT, would see the fruits of the security overhauls in Q3 and Q4 of 2021. And for both of these cybersecurity giants that scenario has materialized as growth has recently accelerated – PANW’s 1Q22 [quarter end 31st Oct] generated 32% YoY growth, and FTNT’s 3Q21 [quarter end 30th Sep] generated 33% YoY growth.
Figure 2 - Sunburst Response Timeline Postulation from Palo Alto Networks: Significant Mispricing
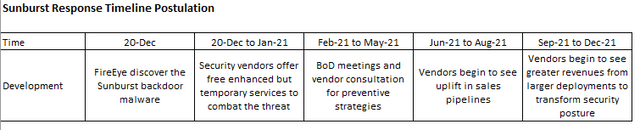
Source: Convequity
What is even more evidential of the SolarWinds event ramifications is FTNT’s 52% YoY billings growth within the Global 2000 enterprise segment for 3Q21 – this has been accelerating for 3 consecutive quarters now. It is this segment that is the most vulnerable to such sophisticated and nation-state funded cyberattacks – mainly because they are prime hacker targets and the IT complexity of their businesses gives hackers the opportunity to target weak spots [e.g., an improperly decommissioned network device] and the size of them gives hackers the scope to ‘live off the land’ and remain undetected. Enterprises need BoB software solutions infused with automation and AI/ML in order to match the attack sophistication, but they also want to avoid further complexity by adding more vendors. FTNT and PANW both have BoB solutions within their comprehensive platforms, meaning CISOs [Chief Information Security Officers] can literally have their cake and eat it.
Security Operations is also becoming widely considered as a necessity in the current threat landscape. Software alone is insufficient which is why leading vendors are ramping up their security services to support their software. Again, FTNT and PANW have impressive Security Operations to compliment their leading platforms and deliver the most dynamic and holistic security service.
We expect the incremental security spend, catalyzed by the Call to Action following the SolarWinds event, to continue throughout 2022 and FTNT’s market-leading TCO [Total Cost of Ownership], performance, and breadth will ensure it continues to be a beneficiary.
Ransomware Surge
The proliferation of ransomware attacks is also pushing organizations to reassess defenses and posture. Trends such as Cybercrime-as-a-Service are giving less skilled threat actors the opportunities to successfully launch ransomware attacks. Moreover, the expanding digital surface due to cloud migration/expansion, and the boom in IoT and OT [Operational Technology] is presenting increasingly more openings for adversaries to target. And criminals are demanding increasingly greater ransoms. These dynamics are forcing organizations to avoid procrastination and address their security asap.
Figure 3 - Ransomware Detection Increases 11x in just 12 months
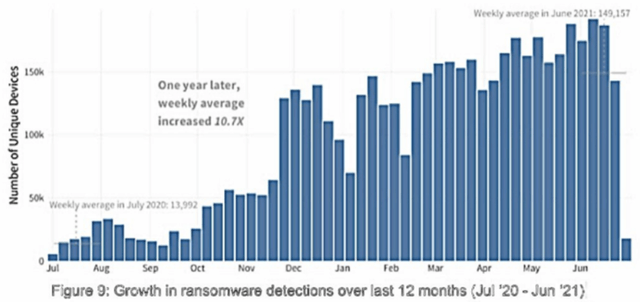
Source: fortinet.com/blog
Ransomware criminals are targeting many of the larger enterprises in verticals that are behind the curve when it comes to modernizing IT infrastructure and security. The May-21 ransomware attack on Colonial Pipeline that caused a temporary energy crisis throughout the Southeast is one of the more well-known events. In Jun-21, JBS, the world’s largest meat producer, was forced to pay a $11m ransom to avoid further widespread supply chain issues. In Feb-21, Kia Motors was extorted to pay approximately $20m in BTC in exchange for sensitive data not to be publicized.
Many of the opportunities for hackers will be in the convergence of IT and OT. This relates to all the Industrial IoT and factory floor systems [the OT] that are connecting to IT systems and the Internet but without the proper security in place. Most of the IIoT, especially in unmodernized verticals, will be dated appliances connecting online that most likely require patches before secure connectivity ensues. This is a big emerging area that FTNT is already capitalizing upon. And given that these verticals will be more cost-conscious than the more modernized type of verticals, FTNT’s market-leading TCO will be highly attractive.
Given the growing abundance of infiltration opportunities, the rise in ransomware sophistication, and the amount of ransom companies are paying, the volume of ransomware attempts will continue to rise. This is heightening awareness and a call to action for organizations big and small.
Figure 4 - Historical and Future Projections of Ransomware Damage Costs
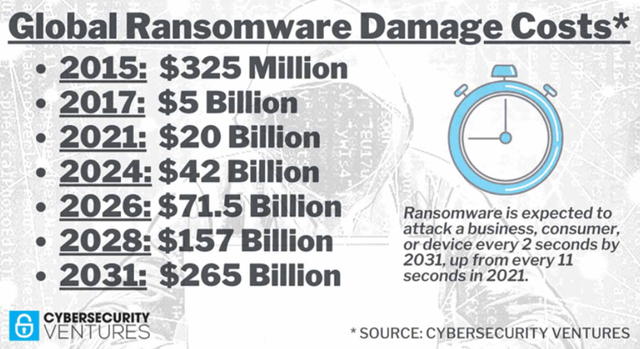
Source: cybersecurityventures.com
To succeed with ransomware, hackers need to move laterally across an organization’s IT infrastructure in order to find valuable data and mission-critical systems. Microsegmentation is an approach to inhibit the unauthorized east-west traffic within an organization which can be adopted by the implementation of NGFWs [Next-Gen Firewalls] at key intersections across the infrastructure.
As mentioned in the November Newsletter, FTNT’s two decades of software/hardware integration has enabled it to pack all the necessary networking and security functions into one affordable and compact device – the FortiGate. The FortiGate can also be implemented in VM form factor. And thanks to its ASIC [Application Specific Integrated Circuit] chip, FTNT has 5x-10x more compute power compared to competitor NGFWs. This compute advantage is particularly magnified within microsegmentation because the number of NGFWs required will add latency. Therefore, microsegmentation with many other NGFW vendors will not be viable. In fact, a young startup called Illumio has the best ROI solution for microsegmentation which utilizes machines’ host OS firewalls – for more information check out our Initial Thoughts report on Illumio we published in October.
These attributes make FTNT the standout leader in price-to-performance and it has the market-leading TCO, which in turn makes FTNT the ideal vendor to implement microsegmentation which is a costly undertaking.
What adds to the alarming nature of the whole ransomware landscape, is that organizations are not aware of what they need to eliminate [or radically reduce] the threats. Despite the news about the security vulnerabilities in using VPNs [the notion that it gives attackers access to the full network], IT decision makers believe VPNs are more useful than Zero Trust in reducing successful ransomware. The majority of ransomware attacks are initially launched via phishing and then the ultimate success of the attack is dependent on the hackers’ ability to laterally move, therefore, secure email gateway, Zero Trust, and microsegmentation should be at the top not toward the bottom of the following chart. This lack of education is another huge opportunity for FTNT – not just for its software but also for the training courses it offers.
Figure 5 - What Technologies IT Decision Makers Believe Will Prevent Ransomware
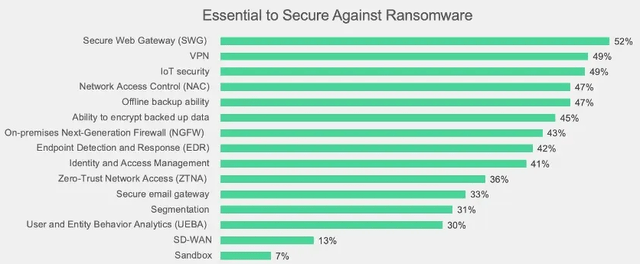
Source: fortinet.com
Biden’s Executive Order
Lastly, heightened awareness and call to action has also stemmed from President Biden’s Cybersecurity Executive Order signed into legislation in May-21. Whilst the order is specifically aimed at software/hardware suppliers that contract directly with federal agencies, in the context of the growing incidence of supply-chain attacks, the order has far-reaching consequences. Just consider the Apr-21 ransomware attack on Apple's supplier Quantas, whereby the attackers targeted a vulnerability in an unpatched Oracle web server to infiltrate Quantas’ systems and then find Apple IP to exfiltrate. Then they demanded $50m and if it wasn’t paid, they were prepared to leak the IP online. This is the type of danger the Biden Administration is trying to avert.
Every company in connection to the federal supply chain will need to fully understand the ramifications of the order. Of particular interest and impact to many organizations is the order’s focus on supply chain software security [a check for vulnerabilities] and improving threat information sharing.
One can imagine the complexities, especially for a large enterprise, in complying with this order, whether a direct or indirect supplier to federal agencies. Naturally, the first port of call for such enterprises as they strive to adhere to the conditions of the order is going to be security companies with BoB solutions, breadth, threat intelligence, and vast amounts of experience. FTNT is the perfect candidate and this has manifested itself in the G2000 billings growth of 52% mentioned earlier. The order also instructs federal agencies to adopt Zero Trust and MFA [Multi-Factor Authentication] frameworks – areas of security in which FTNT has experienced expertise. Federal supply chain vendors have 360 days to comply/adapt to the new framework but given the global ramifications it will likely be an industry tailwind for much longer.
Summary: Heightened Awareness & Call to Action
The following is a snippet of the investment case shown earlier in Figure 1. The SolarWinds response, the ransomware surge [and the limited understanding of ransomware prevention], and Biden’s executive order, have each greatly contributed to an increased awareness whereby organizations have begun to address and harden their security postures. And each of these catalysts will continue to provide strong undercurrents of demand for the foreseeable future. As a result, we view organizations will increasingly look to:
- consolidate vendors in a quest to simplify security operations,
- seek out the BoB solutions rather than aim to cut costs with mediocre alternatives,
- develop stronger relationships with vendors that have proven long-standing reputations for exemplary cybersecurity, and,
- choose vendors that can cost-effectively implement microsegmentation to thwart ransomware attempts.
Figure 6 - Heightened Awareness & Call to Action Summary
Source: Convequity
Fixing the odd security gap isn’t a sustainable approach and will only lead to more point solutions. Companies need to address the security of their entire architecture and adopt a dynamic approach, and hence they need a well-established platform vendor with multiple BoB software solutions and security operation support.
Hybrid Environments
We have all heard over and over again that the world is now in a hybrid environment – a mix of office and home-based work. But to truly understand one of FTNT’s main tailwinds it’s worth digging a little deeper into the whole hybrid movement.
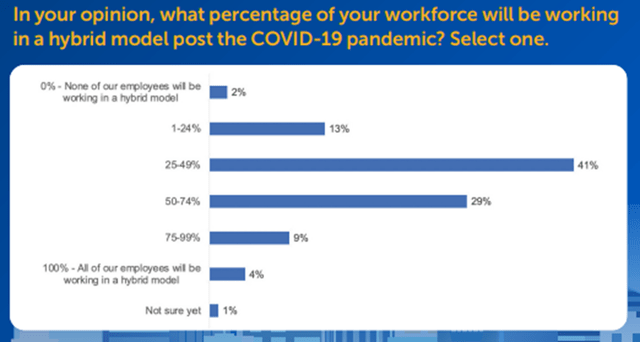
Despite it being common knowledge that hybrid is the future, it’s still useful to consider some recent survey data. A Sep-21 survey conducted by networking provider, Riverbed, consisting of 1,500 participants, shows that the high majority of business/IT decision-makers [BDMs and ITDMs] believe their organizations will adopt a hybrid working model as we exit the pandemic.
Figure 7 - What Percentage of Workforces will be Hybrid Post Pandemic
Source: riverbed.com
42% believe that at least half of their workforce will adopt a hybrid model, which is a huge shift in mindset from Riverbed’s Jun-20 survey which showed that only 16% believed at least half their workforce would adopt a hybrid model.
Hybrid models bring a lot of competitive benefits which has clearly shaped decision-makers’ views. The facilitation of remote work has enabled companies to tap into a broader set of talent sources; it has also lowered costs and enhanced productivity [via reduced commuting].
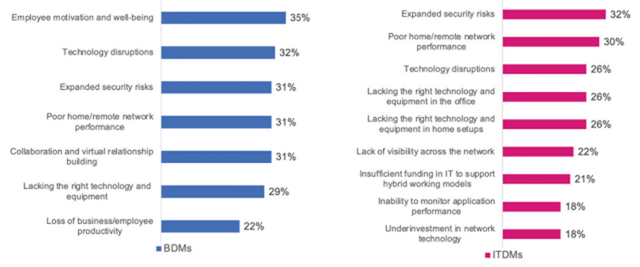
Though, hybrid models also bring in many problems as highlighted in the following chart that shows BDMs and ITDMs main concerns. What is interesting to note is that FTNT’s capabilities in security-driven networking delivers enhanced productivity and security, which will address each one of the ITDM concerns listed in the chart.
Figure 8 - What Are the Biggest Barriers to Sustaining a Hybrid Working Model?
Source: riverbed.com
FTNT’s computing power, Zero Trust, low TCO, and SD-WAN [Software-Defined Wide Area Network] are ideal solutions for all the issues above. SD-WAN is particularly useful because it separates the control plane from the data plane of routers. Network devices, with data and control planes combined, only have information about neighbouring devices, and as a result they do not have network-wide visibility and hence cannot select the optimal paths for traffic. SD-WAN separates the control plane from network devices and centralizes network traffic control. This allows network administrators to set traffic policy for various application types, ensuring mission-critical and latency-sensitive applications are transmitted across the fastest and most reliable transport protocols and along the most optimal routes. Though, SD-WAN not only enhances user experience and boosts workforce productivity, the holistic visibility provides IT admin with the toolset to better secure their network.
FTNT has SD-WAN built into its FortiGate and can also deliver SASE [Secure Access Service Edge]. So, in complex hybrid environments, FTNT’s customers can choose some home offices/branches/stores/data centres/HQ to have an on-prem deployment and others to use SASE, subject to granular requirements. And within such a multi-deployment environment, IT admin will have complete network visibility and policy control that is easy to orchestrate.
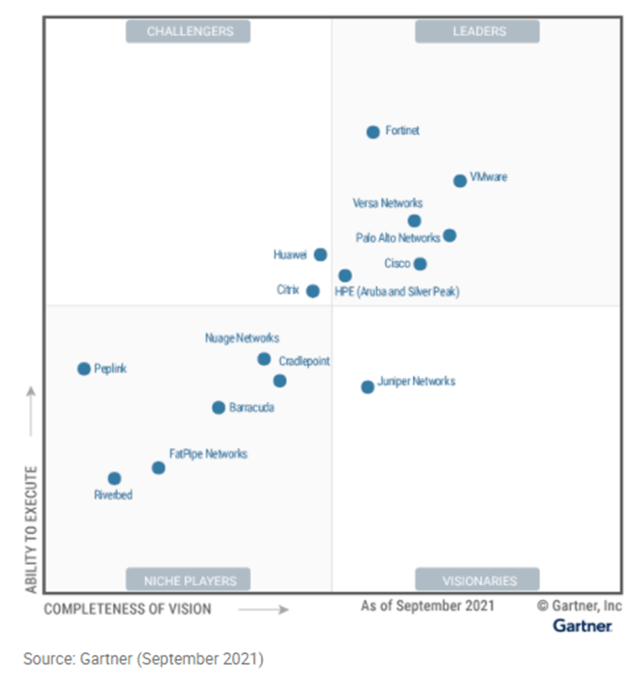
Not only does FTNT have competitive advantages in the SD-WAN market because of their built-in security with Zero Trust, they also have the upper hand in regards to deployments. Thanks to its predominately in-house development and integration approach, FTNT can deliver a smoother deployment and management experience, which is reflected in their standout leadership in the Ability to Execute dimension in Gartner’s Magic Quadrant below. This is a sharp contrast to Cisco’s SD-WAN solution that, according to Gartner, produces a poor customer experience which is in large part attributed to the acquisitions [Viptela and Meraki] they’ve needed to make to participate in the market.
Figure 9 - Gartner's WAN Edge Infrastructure Magic Quadrant [Sep-21]
Source: gartner.com
The following chart is more evidence for the continuing demand for SD-WAN in order for enterprises to enhance productivity across their distributed workforces. And we’ll reiterate that FTNT’s market-leading TCO, superior computing power, built-in Zero Trust, and smoother deployments and management, make its SD-WAN solution a market winner.
Figure 10 - Concerns Regarding Disparities in Network & Application Performance for Remote vs Office-Based Employees
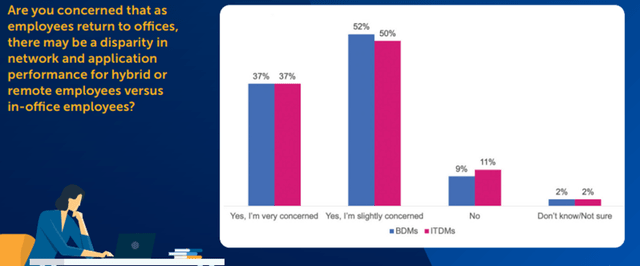
Source: riverbed.com
Below is the last chart we’ll take from the Riverbed survey that shows the intent to invest in the necessary technology to support a hybrid workforce. 42% of respondents intend to make significant investments in the next 12-18 months, which is great news for FTNT and the networking/security industry as a whole.
Figure 11 - Intent to Invest Over the Next 12-18 months
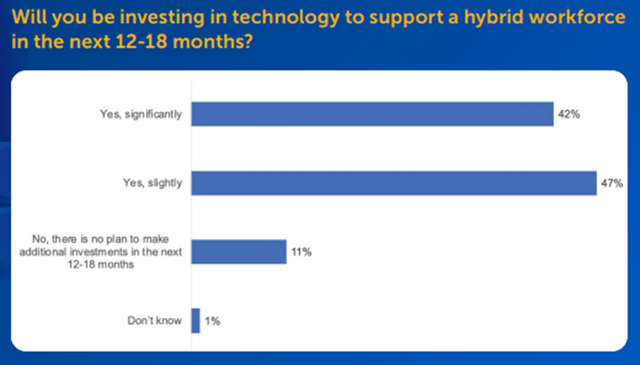
Source: riverbed.com
Summary: Hybrid Environments
The following is a snippet of the investment case shown earlier in Figure 1. Pretty much all the concerns outlined from the Riverbed survey relate to the notion that distributed workforces are causing issues across security, productivity, and visibility. These issues can be resolved with Zero Trust and SD-WAN technology and FTNT is the only vendor that can natively deliver both with home-grown solutions.
Figure 12 - Hybrid Environments Summary
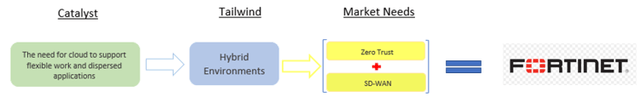
Source: Convequity
Intelligent Connectivity
This tailwind somewhat overlaps with the Hybrid Environments tailwind, though it focuses more on the service provider segment of the SD-WAN market. FTNT is the go-to SD-WAN vendor for a significant portion of the service provider [SP] market [AT&T, Orange, Telefonica, and many more]. These SPs are ramping up investment in preparation for prevalent 5G connectivity and SD-WAN is a key technology for this. A higher number of cell towers, especially for the mmWave frequency band, is required to deliver 5G, and hence there is more traffic management complexity. SD-WAN will help to optimally route traffic to the nearest cell towers to enhance the last mile connectivity.
The reasons these SPs are choosing FTNT for SD-WAN are, again, thanks to FTNT’s market-leading TCO, superior computing power, built-in security, and smooth deployment/management. Investors should expect FTNT to grow revenue as the SPs grow their 5G-enabled networks, and of course, 5G is still very early on in its journey, so this tailwind will contribute to a significant portion of future growth for FTNT.
Figure 13 - Intelligent Connectivity Summary
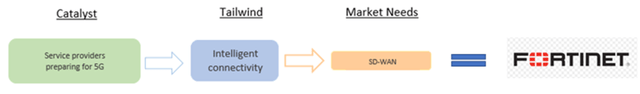
Source: Convequity
Operational Technology [OT]
As companies have been connecting industrial IoT and systems online various issues have arisen:
- Connections are improperly secured due to dated appliances
- IIoT and OT typically have nonstandard OS and hence are not highly compatible with endpoint security solutions
- Visibility is limited because things have been connected in a piecemeal fashion spawning multiple disjointed point solutions for networking and security and thus making companies highly vulnerable to attack
- OT has not been properly connected to the IT systems thus generating effort duplication and more complexity
In essence, OT is generally not secure, since it was originally designed with the assumption it would not be exposed to threats. And as companies have digitally innovated in order to maximize the use of data, they have produced a lot of management complexity and made themselves vulnerable to attack. Remote access to such OT adds further vulnerabilities that companies to need urgently address.
OT attacks can have far more dangerous implications than IT attacks which may instigate more urgency for certain organizations to revisit their security. The purpose of attacking an IT system is to steal data, whereas the purposes of OT attacks are more varied and may result in something like a factory shipping unsafe food because the hacker has corrupted digital safety checks.
In a similar vein to how the SP verticals are driving SD-WAN business for FTNT, we view the less digitally savvy verticals like manufacturing, transportation, and utilities, will drive OT business for FTNT. In the 3Q21 earnings call, FTNT’s CFO Keith Jensen implied that OT currently represents about 6% of total billings, though its growing at 77% and hence investors should expect OT to make more meaningful contributions to the top-line in the near-future.
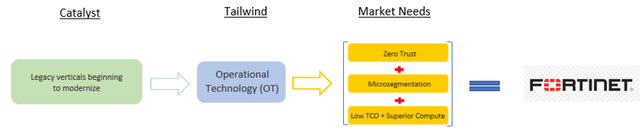
The following snippet from Figure 1 highlights the specific market needs pertaining to OT. Zero Trust is imperative because a primary security flaw that hackers are exploiting to launch ransomware attacks is the access to the entire systems and networks of OT. With Zero Trust, if hackers are highly-skilled they may be able to access one application but they won’t be able to move east-west to look for valuable data and mission-critical systems. FTNT has home-grown Zero Trust capability and in the summer of 2020, they also acquired a BoB Zero Trust cloud startup called OPAQ. Therefore, FTNT are well-equipped to capitalize on the Zero Trust trends.
Microsegmentation goes hand-in-hand with Zero Trust to create east-west barriers for unauthorized users thus greatly limiting lateral movement for hackers. And as previously touched on, these less digitally savvy verticals are likely to be more cost-conscious and have smaller budgets, and hence they will want a security vendor that delivers a low TCO and high ROI. And also, as previously mentioned, microsegmentation isn’t cheap and the number of NGFWs can create notable latency, thus a vendor like FTNT that has low TCO and superior computing power is going to be a prime candidate most of the time.
Figure 14 – OT Summary
Source: Convequity
Valuation Considerations
Relative Valuation
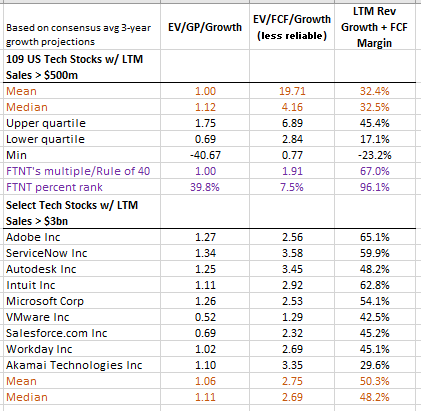
The following table shows that, out of 109 U.S. headquartered software and communication equipment stocks, FTNT’s Rule of 40 is in the top 4% whilst its forward EV/FCF is in the bottom 8% of the distribution [note that the forward FCF is based on expected revenue growth not expected FCF growth]. This is a blatant relative undervaluation, however, FCF can be volatile and hence the undervaluation may be somewhat exaggerated. Therefore, we also like to consider the forward gross profit multiple as a nice compromise between the often-volatile FCF of high-growth companies and the limited insight from sales multiples. FTNT’s forward gross profit is 1.0 which is below the median at the 40th percentile. Again, this shows a significant discrepancy between quality and valuation, and greatly supports FTNT’s investment case.
Figure 15 - Forward Multiples & Rule of 40 Considerations
Source: Convequity
As can be seen from the table, for comprehensiveness, we’ve also compared FTNT to a select group of stocks which have LTM revenue above $3bn and a similar conclusion can be drawn. FTNT has the highest Rule of 40 but it’s forward multiples are below the mean and median – way below in the case of the forward FCF multiple.
DCF Valuation
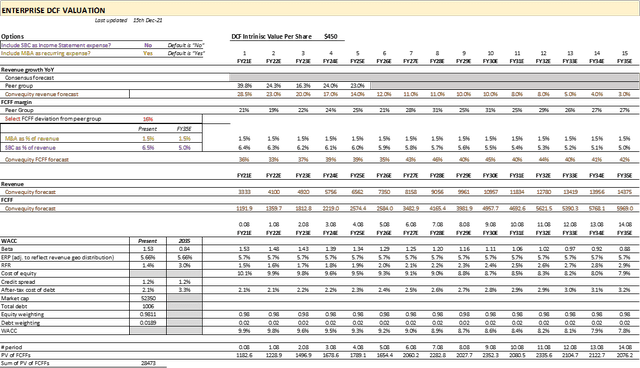
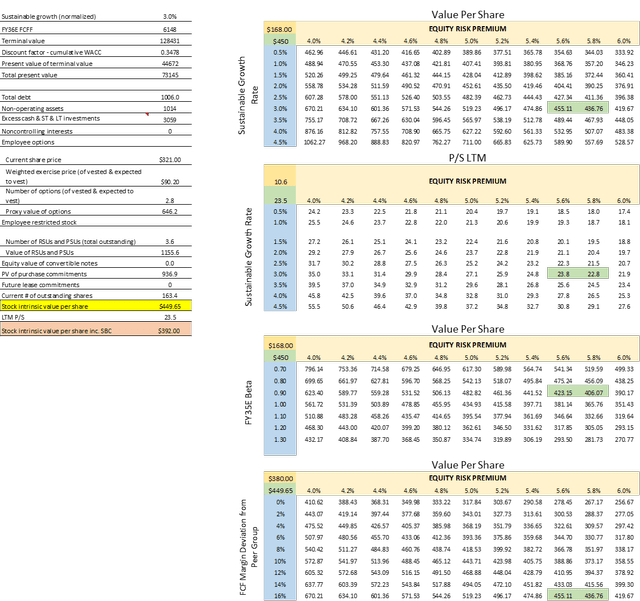
Note: we appreciate the following valuation model may be difficult to see, so please email jordan@m.convequity.com if you want to be emailed the valuation model for a closer inspection.
Given the expected 28.5% growth for FY21 [fiscal year ending 31st Dec], we believe the growth trajectory shown in the following valuation model is not overly optimistic. Also, we think the FCF margin projections are fair considering the TTM FCF margin is 40%. We also think an extended explicit forecast period in which we decelerate growth down to the sustainable rate by FY35 is a conservative parameter. And also take note of the WACC – beginning at a relatively high 9.9% and scaling down to 7.8% by FY35.
The resulting intrinsic value per share is $450, and including SBC in the FCF calculation it is $392. Based on the current price of $321, this represents a 29% discount [inc. SBC] and a 18% discount [exc. SBC]. And FYI, the $450 intrinsic value per share reflects a c. 23x P/S, which is where ServiceNow is currently trading. All-in-all, whilst the parameters are not uber-conservative, we don’t view them as overly optimistic neither. FTNT is not trading at a huge discount but based on the relative valuation considerations and the DCF presented below, we’re still long-term bullish and will look to opportunistically add more shares on strong corrections.
Figure 16 - Valuation Model
Source: Convequity