Themes: OT Security Series (Pt.1) - Securing The Physical World

Summary
- The OT security market is getting hotter and promises to develop into a large submarket of the broader cybersecurity industry.
- Key catalysts for the OT security market are the ongoing ransomware attacks and the recent rate of change in the influence of the CISO.
- There are many players coming from different backgrounds with different strengths and weaknesses; however, our initial research indicates that FTNT's full OT stack advantages give it the long-term upperhand.
Foreword
This is Part 1 of a developing research series on OT security. Just like PANW was the focal point during our cloud security research series, FTNT will be the focal point during this OT security research series. There are striking parallels between PANW's cloud security market positioning and its surrounding competition and that of FTNT's in OT security. Both have full stack security capabilities but are in tough competition with startups offering platform solutions that are easier to deploy but are lacking in depth. FTNT's key rivals in OT are private names such as Armis, Claroty, Dragos, and Nozomi Networks, who were born in the OT world, as well as some publicly listed companies such as Tenable that have expanded from the IT world.
Then, there are other well-known IT security names, such as ZS, who appear to be jumping on the OT security bandwagon, so to speak, as they are lacking OT specific security solutions but still playing the marketing game. PANW is also targeting OT security but its claims are backed up with broad protocol/application support for OT networks. CSCO's vast installed based in OT environments also make it a player to watch. And, also AVGO (Broadcom), is a potential beneficiary of the the blossoming OT market because really they are the only competitor to FTNT's ASIC chips running on switches and routers.
Part 1 is a high level overview of the OT security market - the problems, recent market developments, TAM estimations, and understanding the OT security roadmap and the OT stack. In subsequent parts, we will dive into the specifics of the aforementioned companies, and understand their strengths and weaknesses, with the overall goal of better understanding FTNT's long-term prospects in OT and further refining the stock's investment thesis.
Key Terms
OT (Operational Technology) - broad category that includes any technology used to control or monitor physical processes and devices.
ICS (Industrial Control Systems) - a major subset of OT focused specifically on the control of industrial processes that are mission critical to the business.
IIoT (Industrial Internet of Things) - sensors and actuators that send systems data about industrial equipment.
Introduction
OT security has been a small niche within cybersecurity for over ten years now. It is a very specialized area of cybersecurity, quickly becoming critical to drive forward the Industry 4.0 evolution. OT security aims to protect OT as industrial environments converge with IT environments and connect to the Internet, to drive greater business agility and competitiveness.
OT, and more specifically, ICS and IIoT, generate voluminous amounts of data that traditionally have not been utilized. However, when connected online and to the enterprise's IT environment, this data can be harvested and analyzed in order to improve the quality and speed of industrial operations and deliver better business outcomes. This is the underlying driver that is persuading many unmodernised companies and verticals to ramp up their digital transformation.
Prior to this digital transformation trend, OT environments were relatively simple to secure. Various network segments would be completely air-gapped and disconnected. Any communication with IT would be tightly controlled along a single pathway. Moreover, there were no devices open and facing the Internet. But when these OT environments began merging with IT and leveraging the Internet to generate richer insights for the business, they did so without security as a primary consideration.
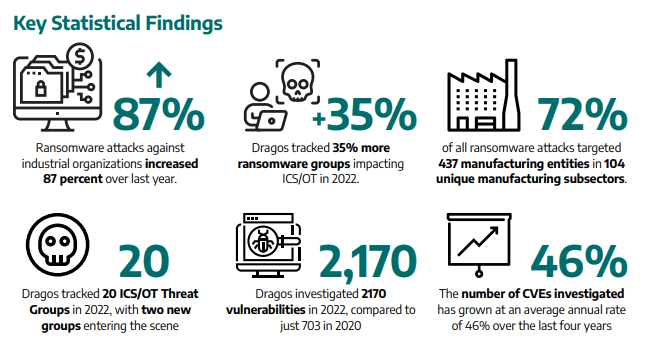
The pandemic forced companies in verticals, such as manufacturing, utilities, and energy, to accelerate their digital transformation in order to become more competitive. This rush to digitalise with little consideration for security, has left them highly exploitable to cyber attacks. Because of this, OT environments are becoming increasingly targeted by cybercriminals, especially ransomware groups. According to OT security specialist Dragos, in 2022, the number of ransomware attacks targeting OT increased 87% and there were 35% more ransomware groups impacting OT. The high value production environments in which OT controls, in conjunction with their inherent vulnerability, make them prime targets for ransomware groups.
In Part 1 of the OT Security Series, we are going to take a high-level view of the industry, covering the folllowing:
- Review the problems that orgs face when digitalising their OT environments.
- Consider the catalysts that are driving the renewed interest in OT security.
- Assess the TAM size of the market, calibrating our own estimates with secondary market research.
- Discuss the roadmap and networking/security stack of OT security.
- Discuss whether or not some OT claims by vendors are marketing games (i.e., Zscaler).
- Conclude with the key players we plan to research during the OT series and share initial thoughts on FTNT's long-term prospects.
The high-level overview of the industry in Part 1 will lay a solid foundation for us to dive deeper in subsequent reports, into the strengths and weaknesses of each key player and better evaluate FTNT's prospects in this promising new cybersecurity segment.
The Problems
OT equipment was previously disconnected from the corporate network, thus no cybersecurity was necessary. The emergence of 4G, IIoT, and then Covid-induced remote operations, exposed critical physical infrastructure to the IT network, and sometimes directly exposed it to the public Internet.
For maximum impact, cybercriminals aim to target ICS, which are the mission critical systems controlling industrial processes. Compromise of such systems, whether it be a power grid or water sanitation facility, not only jeopardises the operating company but can also endanger the public. Therefore, as they become more connected, it is imperative to secure them; however, there are several problems:
- More devices and more connectivity (to IT, to the cloud, via the Internet, remote access) are exposing dated equipment and patch-needing software to the Internet. This is leading to a surging rise in cyber attacks.
- The endpoint devices within ICS are constrained in regards to compute, storage, networking, and power. So, oftentimes, it is not possible to install an agent like it is for endpoints in an IT environment.
- Even if some ICS endpoints did have the resource capacity to have an agent installed, because of the non-standard operating systems and outdated hardware/firmware, agents from IT will not be compatible.
- The non-standard OS' and dated hardware/firmware also make it more difficult to enumerate the network - that is, collating information about hosts, open ports, OS', services, etc. This means there are likely many blind spots within OT networks.
- Due to a lack of agents installed on ICS endpoints, telemetry is scarce compared to IT environments. This makes SOC activities such as EDR more challenging.
- ICS hardware has been designed to run for decades before it is replaced and hardware and software are tightly coupled together. This makes updates and upgrades of the software very difficult, to the point whereby it may not be updated for many years, thus making the ICS vulnerable to attacks.
- Many OT/ICS equipment were designed long before WAN and Internet connectivity were even on the horizon. Hence, they were not built with a secure-by-design philosophy. This means many OT/ICS protocols do not have the built-in security features as many IT counterparts.
- Oftentimes, the OT/ICS operators will be aware that a piece of software needs patching but they cannot do anything about it due to hardware upgrade prerequisites or due to lack of vendor support. Moreover, unlike the IT ecosystem, there isn't wide community support to help OT operators patch software vulnerabilities.
- Even if a patch is available for a software vulnerability, it might not be possible to do because the machine in question is mission critical and therefore downtime is not an option.
- Historically, OT security has been implemented by OT/ICS operators rather than security specialists. As their performance is measured based on operational performance, it is no surprise that they have cut corners and dedicated less time in implementing the appropriate security defenses.
- Compared to an IT breach, an OT breach has the potential to be far more damaging, often leaving the victim no choice but to pay the ransom. An IT breach may lead to privacy violations, corporate embarrassment, and service disruption, though an ICS breach can impact the health and welfare of the public.
- In a similar vein to how cloud adoption has brought major flux to corporate networks, as more OT equipment is digitised and automated, this is going to continue expanding the attack surface. This is a multi-decade theme if you acknowledge that eventually robotics will replace most manual jobs across the industrial sector.
Generally, OT environments are easily exploitable due to a lack of specialized security solutions and because of the challenges associated with patching vulnerabilities. There are strong parallels with the adoption of cloud computing, whereby orgs migrate their data, applications, and operations to the cloud, and think about security reactively rather than proactively. And because security architectural components and best practices weren't built in as they migrated, orgs soon became highly vulnerable due to misconfigurations across cloud infrastructure and networking components. Furthermore, the velocity of new software and the complexity of software supply chains within cloud environments, has led to many more software vulnerabilities that attackers exploit.
Likewise, a similar pattern is playing out as industrial companies digitalise their OT. First, they are connecting their OT, ICS, and IIoT to their IT and cloud environments, often using the Internet as the conduit, and then thinking about security afterwards, or even worse, when an incident or breach has occurred. Although, we think that the higher stakes of OT breaches versus cloud breaches (along with the numerous high-profile and damaging OT breaches of late) will likely expedite deep security planning faster than it has occurred in the cloud. In general, OT modernisation has exposed the various preexisting vulnerabilities to the outside world, and ransomware gangs, in particular, are enjoying great success because of it.




