Area 1 – Cloudflare’s Secret Weapon For SASE Success

Summary
- In April 2022, Cloudflare acquired next-gen email security startup, Area 1 Security.
- Area 1 has a truly cutting-edge technology stack geared toward offensive/preemptive security – similar in philosophy to shift-left but for combating email-based attacks.
- Combined with NET’s talent, culture, and global network, Area 1 has the potential to deliver huge value for orgs defending themselves against email-based attacks.
- As we take on board all the insights within this report, we’re confident Area 1 can be a key catalyst for NET gaining market share in SASE & Zero Trust.
Intro
Email security is an intriguing area within the larger cybersecurity industry. Most email-based attacks can be stopped with a NGFW (Next-Gen Firewall). For instance, NGFWs (and SWGs) have URL filtering to prevent an employee from connecting with a malicious webpage after they’ve clicked on an email link. Many NGFWs also include DNS security, which interoperates with email security protocols such as SPF, DKIM, and DMARC, in order to thwart any email exchange with domains owned by bad actors.
However, as email has become such a colossal attack vector, email security can no longer be satisfied as just an addon solution, or with a peripheral focus. According to CISA (Cybersecurity & Infrastructure Security Agency) and many other reports, 90%+ of cyberattacks begin with email-based phishing, and many of these manage to evade the defenses built into the NGFWs. Cybercriminal techniques such as DNS poisoning and DNS hijacking can fool DNS security systems, and URL filters are often too slow to blacklist the very latest malicious webpages.

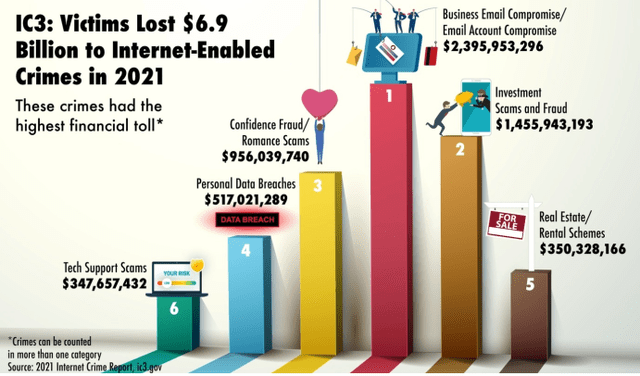
Furthermore, attacks like BEC (Business Email Compromise), contain zero malicious payloads/files/URLs, and hence cannot be detected by traditional methods. A BEC attack involves the cybercriminal hacking into an email account (usually by purchasing stolen credentials on the dark web), observing the email correspondence, and then at the opportune time they begin sending emails from the account they’ve hacked. Usually, they will target C-level email accounts, and send a fake invoice to someone in the finance department and generate a sense of urgency to make the payment to a bank account controlled by them. According to the FBI, this attack type alone cost U.S. orgs $1.8bn in 2020. In 2021, the damage of BEC attacks was even greater.
The reconnaissance of BEC and related sophisticated phishing attacks, are predicated on advanced social engineering, and the execution is based on trickery. This largely renders rules-based detection methods obsolete, and instead, solutions to combat these threats need to be built on AI/ML.
Legacy providers, like Proofpoint and Mimecast, still dominate the email security market; however, they are at major disadvantages when it comes to protecting against BEC attacks with high efficacy. This is largely because it’s extremely difficult to refactor software with a long history to be more conducive to AI/ML. Of course, such legacy vendors need to claim they can fully protect against BEC attacks, but that is just marketing survival. In reality, legacy names can’t compete with the efficacy of next-gen email security players such as Area 1 Security. And we think it’s likely there will be a gradual disruption to the email security industry, whereby we see an increasing spotlight unveil that incumbent players aren’t capable to fully defend against these advanced socially engineered attacks.




